

Welcome to your weekly Expert Insights News Roundup.
In this new series we’ll wrap up the biggest news of the week in five minutes or less.
Have a story to share? Contact [email protected].
1. Polling Day Is (Almost) Here

There are less than 24 hours to go until polls open in the US Presidential election.
Axios reports that campaigns are under pressure as hackers, nation-state spies, and cybercriminals attempt to target the integrity of the US election process via hacking and digital disinformation.
China-backed hacking groups have targeted Trump family members and campaign aides, reports the New York Times.
Meanwhile, US government agencies have accused “Russian influence actors” of faking a video purportedly showing Haitians illegally voting in Georgia (ABC News).
A joint statement from the Office of the Director of National Intelligence, the FBI, and the Cybersecurity and Infrastructure Agency (CISA) said:
“The IC assesses that Russian influence actors manufactured a recent video that falsely depicted individuals claiming to be from Haiti and voting illegally in multiple counties in Georgia.”
In a race where the final result is looking likely to be very tight, there could be plenty more opportunity for disinformation campaigns in the weeks ahead.
2. 2024 Is Likely To Be A Record Year For Ransomware
Ransomware has continued to surge in 2024, Recorded Future’s Allan Liska told TechCrunch during a panel this week.
“The curve is going to flatten a little bit, which I guess is good news. But a record-breaking year is still a record-breaking year,” TechCrunch reports.
Earlier this year, Expert Insights spoke to Zscaler’s Senior Director of Threat Intelligence, Brett Stone-Taylor, who reported that ransomware attacks were up 18% year-on-year according to Zscaler’s threat data.
In addition, they had tracked the single biggest ransomware payment ever made- an eye-watering $75 million USD payment.
Basic IT hygiene and security awareness training are a good starting point for protecting your business against ransomware attacks, Stone Taylor recommends.
3. Multiple UK Councils Hit By DDoS Attacks
Last Monday, multiple councils in the UK were hit by distributed denial of service (DDoS) attacks (BBC News).
A pro-Russian hacker took responsibility for the attacks, posting on X that the attacks were launched due to UK Government support for Ukraine.
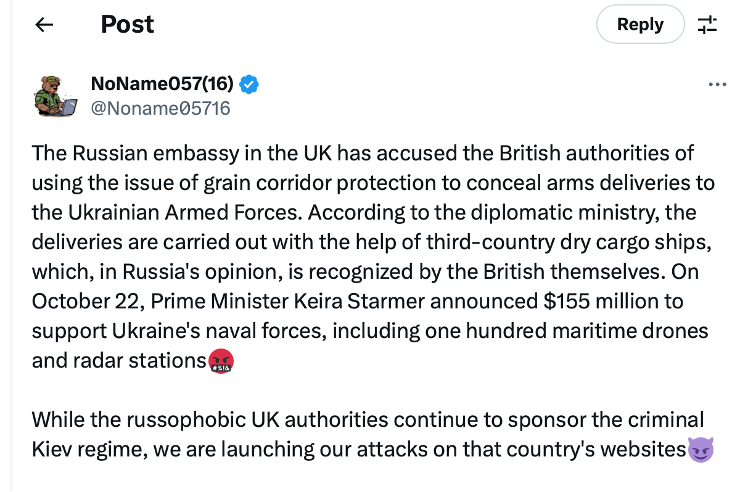
At least seven local council websites were affected, including Salford, Trafford, and Dudley. At the time of writing all have fully recovered, reports Infosecurity Magazine.
In a DDoS attack, a threat actor directs an overwhelming amount of traffic to a website or web app. This influx of traffic causes a sudden surge in demand ultimately crashing the server so that genuine end users and customers can’t interact with it (Expert Insights).
Businesses should invest in robust network security tools to ensure their digital services are kept secure against DDoS attacks.
4. Chinese-Backed Hackers Breached Over 20 Government Networks In Canada

Threat actors sponsored by China infiltrated at least 20 Canadian government networks over the last five years, reports CBC News.
The hacker groups reportedly “compromised” several networks and were able to access valuable information, according to a report from the CSE, Canada’s cyber spy agency.
The report named the People’s Republic of China as the “most comprehensive cyber security threat facing Canada today.”
The report outlines that Chinese state-sponsored actors are repeatedly conducting cyber espionage campaigns against government networks in Canada.
India, Iran, and Russia were also named in the report as “cyber adversaries” very likely to target “government, military, private sector, and critical infrastructure networks.”
5. Disney Restaurants Hacked By Disgruntled Ex-Employee

A more bizarre story to close for this week – a former Disney employee has been accused of illegally hacking company systems, reports SC Media.
A former system admin is facing charges of computer fraud after a series of attacks targeting restaurants at Disney’s theme parks.
Reportedly, the ex-employee was terminated by Disney in June, but over the next three months continued to access systems used to program digital signage from restaurant menus.
The attack started with somewhat goofy revenge pranks – for example, changing menu prices or adding profanities to item descriptions.
But eventually, the entire menu system was rendered inoperable for over a week – forcing employees to resort to handing out menus on paper.
Insider threats and attacks by former employees have become a major business concern. In fact, 75% of insider cyber-attacks are carried out by former employees.
We recommend all organizations have strong identity and access management and privileged access management solutions in place to make sure that employee credentials are rotated whenever a new employee joins or exits.
We’ll be back on Thursday (November 7) for our cybersecurity vendor news roundup. Until then! 👋
Expert Insights Cybersecurity Resources
- The Top RMM Solutions For MSPs
- The Top Mobile Device Management (MDM) Solutions
- The Top Email Security Solutions For Office 365
- The Top Email Security Gateways
- The Top Multi-Factor Authentication (MFA) Solutions For Business
- The Top Phishing Protection Solutions
- The Top Cyber Threat Intelligence Solutions



