
Microsoft 365 Email Security: How To Stop Phishing Emails
Sponsored Content: Why an integrated cloud email security solution is the best way to block phishing emails in Microsoft 365.

Quick Answer – The most effective way to prevent phishing emails in Microsoft 365 is to implement an Integrated Cloud Email Security solution (ICES). Integrated Cloud Email Security solutions analyze all email content to detect phishing content and automatically remove malicious emails from all affected user inboxes.
ICES solutions complement the native email security controls within Microsoft 365 to prevent phishing without the need to deploy any complex software or hardware. Key features include:
- Detailed Email Analysis: ICES solutions analyze all inbound, outbound, and internal email content using machine learning , AI and sandboxing to detect advanced email threats.
- Instant Remediation: API-based integration with M365 means threats are instantly removed across the tenant with one click, with little to no delay, even if an email is found to be malicious after delivery to the inbox.
- Faster Deployment: ICES solutions can be easily deployed via API without needing MX-record changes. There are no issues with email rules or deliverability. Skip to our tips on choosing the right ICES solution.
We highly recommend that organizations implement an Integrated Cloud Email Security solution as the best way to prevent phishing and business email compromise attacks, along with native anti-phishing controls available within Microsoft 365 by default, such as multi-factor authentication (MFA).
In this article, we’ll cover how phishing works, the native controls available within Microsoft 365 to minimize the risk of phishing emails, and how to choose the right ICES provider. Learn more about our recommended ICES solution PhishTitan.
How Does Phishing Work In Microsoft 365?
Phishing emails are malicious messages that impersonate legitimate brands or individuals in order to trick users. They can range in sophistication from low-level attacks that target millions of inboxes, to highly sophisticated campaigns that impersonate high-level company executives.
Microsoft 365 is an enterprise office service, so many phishing emails are based around financial fraud. Some common phishing tactics include:
- CEO Fraud: A cyber fraudster impersonates a company CEO and email employees to ask them to approve a fake purchase or buy gift cards. This is a very common scam.
- Credential Theft: Cyber-criminals impersonate a brand and send a fake login page via malicious URLs within an email. When a user logs in, their legitimate email address, passwords or card details are harvested by the fraudster.
- Business Email Compromise: Cyber-criminals impersonate a trusted supplier or partner and send a fake invoice. This can be hugely costly and can involve actual compromise of email accounts. This is often a targeted and sophisticated scam – but is still all too common.
Phishing attacks often leverage email spoofing techniques. This involves attackers forging email headers, so they appear to come from a legitimate sender address. This could involve replacing the letter “O” with a “0,” for example, something that many users would not easily notice at a quick glance.
Phishing can also quickly spread, especially when account compromise is involved. If an attacker is able to harvest a user’s Microsoft 365 credentials with a fake landing page, they are then able to send out phishing emails from the infected mailbox. This often also enables access to other internal services and applications, leading to serious data breaches within an organization.
Microsoft 365 Phishing: 5 Stats To Know
- Phishing is the number one recorded internet crime (FBI)
- An estimated 3.4 billion phishing emails are sent every single day (ValiMail)
- Around 36% of all data breaches involve phishing (Verizon)
- The average cost of a data breach that starts with phishing is USD $4.91 Million (IBM)
- 81% of organizations have seen an increase in phishing attempts since 2020 (McAfee)
Why Do Attackers Target Microsoft 365?
Microsoft 365 is one of the most commonly targeted platforms for phishing attacks. This is because it’s such a widely used platform in the business space, with around 3.6 million customers worldwide.
It’s also very cost effective for attackers to purchase Microsoft 365 domains and test phishing campaigns. Stolen credentials themselves are widely available to purchase on the dark web, and phishing attacks can be quickly launched to millions of inboxes used by M365 users.
It’s critical that organizations have strong defenses in place against phishing attacks. As the statistics above demonstrate, even low-effort phishing campaigns can be hugely costly to organizations, and, in severe cases, can be the starting point for major customer data breaches that can potentially be business threatening.
Why Is It Difficult to Stop Phishing In Microsoft 365?
From an end user’s perspective, it can be very difficult to spot a phishing email. The most effective fraudsters will make great efforts to make phishing emails look as realistic as possible. Even seasoned cybersecurity experts can find it difficult to differentiate between a fraudulent and a genuine email message. Phishing works because it plays on innate human weaknesses – it’s easy for us to make mistakes, especially at times of stress.
“We’re in a world where people are doing multiple tasks at once. Attackers are utilizing a lack of focus and trying to engage people in phishing emails; by our nature, we’re social beings, so we see an email and we want to engage with it.” – Conor Hynes, Director of Product Management & Data Strategy at TitanHQ
On the technical side, phishing can be difficult to prevent because phishing emails often do not contain actual malware or harmful content. Traditional email filters, such as Secure Email Gateways use a static rules-based approach to identify “known good” and “known harmful” email content. Harmful content could include a malicious attachment, harmful URLs, or a risky sender domain, and if flagged, the email would be blocked from delivery.
Phishing emails though are simply plain text emails, often sent through legitimate mail domains that would not generally be flagged as harmful. Phishing emails often include web links to phishing websites – but these may not be dangerous at all during the initial time of delivery. Devious cyber-criminals will wait until the email has been safely delivered to users before injecting the previously safe webpage with malware, once it has already bypassed the email filtering software.
In short – phishing scams are popular because they are cheap and relatively easy to conduct. They can hit millions of people and then be finely targeted to maximize revenue for attackers. They are also difficult for cybersecurity teams to prevent, evading traditional email security controls and targeting the end user directly. So how can we best protect employees against these email threats?
Native M365 Anti-Phishing Email Policies
Microsoft 365 does, by default, offer features to defend against phishing attacks. Exchange Online Protection (EOP) is a cloud-based email filter that is designed to block spam, malware, and some phishing threats.
With EOP, anti-phishing protection features include using spoof intelligence to review fraudulent email senders and enables admins to manually block or allow suspicious messages. EOP also reviews the sender’s DMARC authentication, and analyzes other sender attributes such as reputation, sender history and more to prevent delivery of malicious email messages. Within M365, admins can also tune anti-phishing policies and view status and threat reports.
Exchange Online Protection provides a good level protection against basic email phishing and spam, but it is not designed to prevent advanced phishing and BEC attacks. For example, it does not include many of the advanced features of third-party email security tools, or indeed Microsoft’s own ‘Defender for 365’ solution, an add-on email security service designed to provide greater protection against phishing and impersonation attempts.
For these reasons, security experts recommend that organizations looking to protect against phishing should enhance the native security controls available in M365 with a third-party email security solution. The most effective way to combat phishing in M365 is to implement an integrated cloud email security solution.
How Do Integrated Cloud Email Security Solutions Work?
Integrated Cloud Email Security solutions analyze all inbound, outbound, and internal email content using multiple threat detection engines including Natural Language Understanding (NLU) and Natural Language Processing (NLP) to identify and stop phishing emails. ICES solutions are deployed via API connection to cloud email services, and can, therefore, remediate malicious emails in real time, even after they have been delivered to users.
ICES solutions also provide in-line banners on email messages warning users about suspicious or unknown email sender, helping improve user awareness of phishing attacks. Users can report any suspicious email content directly from the inbox, helping admins to faster identify and remediate threats.
Because ICES solutions work directly within the email service, e.g., M365, they have full visibility of all internal email traffic. Using AI/ML processing, they can use this knowledge to identify suspicious email messages that deviate from users’ previous behaviors, providing a better overall level of protection than static gateways, which can only analyze one email message at a time.
With an ICES solution, admins can configure email policies and remediate threats instantly by deleting harmful email messages from all inboxes, even after delivery. For these reasons, ICES are much more effective at stopping phishing attacks and identifying compromised mailboxes.
How Do Integrated Cloud Email Security Solutions Stop Phishing?
ICES solutions use multiple methodologies to prevent phishing attacks and identify account compromise. When an email is delivered to your M365 environment, the ICES system will use machine learning and natural language understanding, combined with threat intelligence, to look at hundreds of attributes or ‘signals’ to assign a risk score in real-time.
Depending on the ICES solution, these can include:
- Account login details, such as unusual login locations, time-of-date, or device
- Email filter rule changes that may indicate an account compromise
- Sender information, such as name, email address, if the sender is a new contact, or an old contact name with a new email address
- Suspicious attachments, such as an invoice sent on the first email communication from a new vendor
- Attachment and URL sandboxing to identify malicious URLs and attachments at time of click
- Tone of voice and language processing, for example urging immediate action or fast transfer of funds
When these signals flag an email as potentially harmful, admins can choose to either block the message outright, or have the email delivered with a warning banner to the end user. This is typically based on the severity of the risk score identified. Another benefit of ICES solutions is that users can report phishing directly from their email inbox, which further improves threat detection. Learn more about our recommended ICES solution PhishTitan.
ICES Vs. Secure Email Gateway: What’s The Difference?
Many will be most familiar with email security in the form of the Secure Email Gateway or SEG. In the past, SEGs would have been on-prem appliances which would plug into the email server and filter messages before delivery to client mailboxes. Now, they are more commonly delivered as cloud services, where email messages are routed via the filter, before being delivered to users.
Email gateways are highly effective at blocking spam and malware, but are less effective at stopping targeted phishing and account takeover attacks as they cannot provide the deeper email analysis required to prevent sophisticated phishing attacks. For this reason, ICES evolved originally to compliment the capabilities of the SEG, but ICES tools are now increasingly replacing the SEG altogether.
“Traditional email filters stop emails in bulk before they ever enter the inbox, where it’s quite difficult to actually do the analysis that’s required to stop phishing. It’s not a fault of traditional email solutions; it’s just that they weren’t built to deal with sophisticated phishing attacks.” – Conor Hynes, Director of Product Management & Data Strategy at TitanHQ
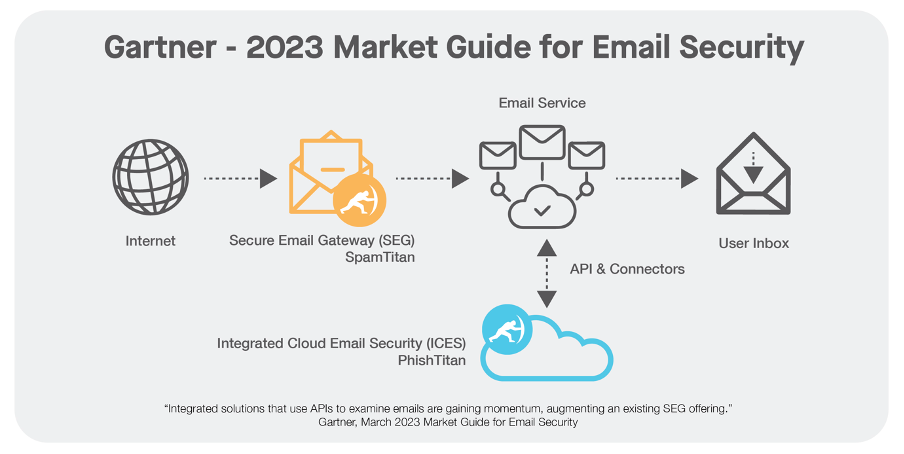
Benefits of ICES solutions over the SEG when it comes to phishing include:
- Defense in depth: ICES solutions provide multiple layers of threat protection and can be used in conjunction with native email security controls and even alongside a SEG itself. Traditional email gateways however replace native email security controls.
- AI powered phish protection: ICES solutions provide better protection against phishing, account takeover, and email compromise using AI to analyze user and inbox behaviors and remove threats in real time.
- User training: ICES solutions provide better protection for end users, with in-line email warning prompts and the ability for users to report phishing emails directly within the email inbox.
- Easier deployment: As ICES solutions are deployed via API, they can be rolled out instantly. SEGs, on the other hand, require MX-record and mail flow rule changes that can be complex.
- Lower support overhead: ICES solutions are very easy to use, configure, and view reports. Traditional SEGs are more difficult to manage overtime, and do not work natively with cloud email platforms in the same way as ICES solutions.
How To Choose The Right ICES Solution To Stop M365 Phishing
ICES solutions provide better protection against phishing, account takeover, and email compromise. The market has become highly competitive, with a number of solutions available to compare. When choosing an ICES, here are the most important considerations to make. This list is based on our own interviews with technical representatives from many of the leading ICES providers:
- Multilayered Protection: Multiple levels of phishing detection are crucial, including NLP, AI-analysis, URL and attachment sandboxing and anti-virus
- Business Email Compromise (BEC) Protection: Analysis of user and sender behaviors to detect compromised email accounts
- Threat Intelligence: The best vendors leverage extensive threat intelligence feeds that pick up on new and emerging phishing threats to provide strong protection
- Time of Click URL Protection: It’s important to protect against malicious URLs at time of click them to prevent users accessing malicious web content
- Report Phishing In Outlook: End users should be able to view warning banners and report risky emails directly from their email client, on desktop or mobile
- Integrations With M365: API-based deployment with M365 means much easier deployment and lower management overhead
- Management Console: Consider the ease of use, policies, and reporting available in the management console
- Vendor Reputation: We recommend working with a trusted provider in the email security space, with a strong reputation in the industry
Introducing PhishTitan
PhishTitan is an integrated cloud email security solution that delivers real-time protection against phishing, malware, and other credential-based email attacks. The solution is designed to work natively with Microsoft 365 and blocks the sophisticated email threats that may evade Microsoft’s native email filters. Get a demo of PhishTitan.
PhishTitan delivers key phishing protection features:
- AI-driven phish analysis: PhishTitan’s unique large learning models (LLMs) are used to block zero-hour phishing attempts and reduce false positives
- Time of click URL protection: Clicks are scanned for malware in real-time, when clicked by the user
- One click remediation: Admins can remediate phishing emails across your entire tenant in just one click
- In-line warning banners: In line warning banners warn users of suspicious email messages. Users can report emails directly within the outlook client
- Link lock service: If a URL is found to be malicious, the user will be directed to a blocked page, preventing access to harmful websites
- Smart mail protection: Compares inbound email messages against known email threats to protect against current phishing scams
- Data loss prevention (DLP): Prevents internal employees emailing out sensitive internal data, mistakenly or intentionally
- Curated threat intelligence: Extensive threat intelligence feeds are used to identify emerging email threats
- Comprehensive reporting and insights: Detailed security reports and insights into inbound email threats and email usage per user
- Native integration with M365: API-based integration means deployment to M365 takes just a few minutes
PhishTitan is developed by TitanHQ, an award-winning email security provider based in Galway, Ireland with teams across North America and Europe, supporting over 12,000 businesses and 2,700 MSPs. Alongside PhishTitan, they offer a range of popular email security services for SMBs, including an email gateway (SpamTitan), DNS web filter (WebTitan), email archiving (ArcTitan), email encryption (EncryptTitan) and security awareness training (SafeTitan).
Watch: PhishTitan Overview – Powerful protection for Microsoft 365
How PhishTitan Stops Phishing In Microsoft 365
PhishTitan uses AI-driven algorithms to analyze all email messages in real-time. Their threat inspection systems scan email content to look for phishing or account compromise indicators. These signals can include sender reputation, email content, and comparisons with the latest phishing threat intelligence.
When a suspicious email is detected, it is flagged with a customizable warning banner directly within the email client. This prompt warns users not to engage with the email, click on links, or agree to make any payments. This rapidly reduces the risks of phishing, ransomware, CEO fraud and other credential-based email threats.
As Conor Hynes, Director of Product Management & Data Strategy at TitanHQ explains: “Phishing isn’t about just detecting emails; it’s about educating end users […] The best time to educate and train a user is at that point of interaction. So, they see an email, they see it’s been bannered, they see that the email has a malicious link, and they begin to understand what a phishing email looks like.”
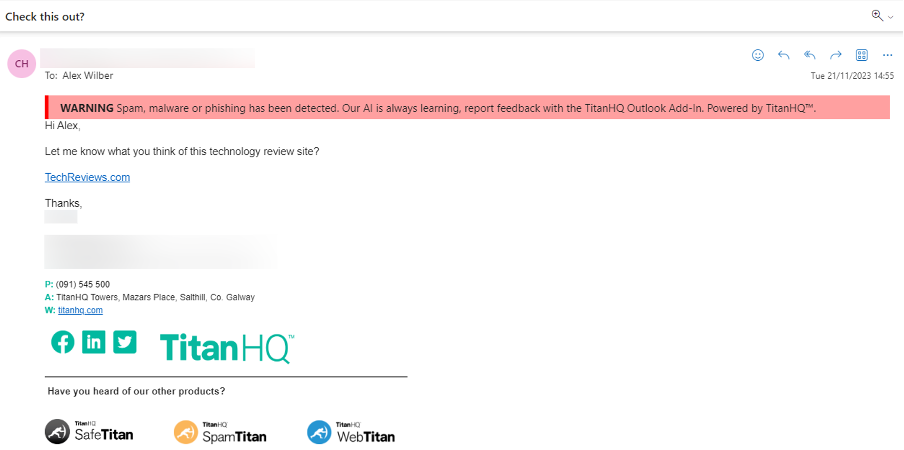
PhishTitan uses the Microsoft 365 API to integrate seamlessly into your email environment. This means the phishing protection is applied to all users in just a few minutes, for all inbound, outbound, and internal email messages. Get a demo of PhishTitan.
Other Important Security Tools To Stop Phishing In Microsoft 365
Alongside the ICES solution, we do recommend that the absolute best security for M365 can be achieved with a multi-layered email security approach. This involves using multiple tools to protect users and defend against phishing attacks however they materialize. These tools can include:
Secure Email Gateway: ICES solutions can be used to either replace or augment the traditional secure email gateway. Email gateways scan email content for malicious content, and automatically quarantine phishing emails.
Phishing Simulations and Awareness Training: Phishing and security awareness training solutions provide realistic phishing simulations and training to end users, helping to improve their ability to spot and report real phishing attempts.
Email Encryption: Email encryption solutions automatically encrypt emails containing sensitive information or about important transactions. This makes it harder for attackers to compromise email networks and conduct targeted spear-phishing attacks.
DNS Filtering: DNS Filtering blocks users from visiting risky or malicious web URLs. This includes phishing landing pages designed to harvest login credentials.
DMARC: Domain-Based Message Authentication Reporting and Conformance (DMARC) authenticates emails have been sent from a legitimate domain. With DMARC, you can prevent cyber-criminals using your domains to send out spam messages.
Multi-Factor Authentication (MFA): MFA is absolutely critical to mitigate against phishing as it prevents unauthorized users from logging into your M365 accounts. Ensure two-factor authentication is switched on for all M365 users.
Alongside PhishTitan, TitanHQ addresses many of the above product areas, with solutions including:
- SpamTitan: A leading secure email gateway offering virus protection, reporting and email validation.
- SafeTitan: Behavior driven security awareness training offering real-time phishing simulations.
- EncryptTitan: A fully featured email encryption service to meet compliance requirements and protect email data.
- WebTitan: A DNS security solution providing advanced web protection and web content filtering controls.
Summary
Phishing emails continue to be a major business risk, costing victims billions each year. As organizations continue to adopt cloud-based email platforms such as Microsoft 365, they must invest in a strong solution to defend their employees against harmful phishing attacks.
Integrated Cloud Email Security solutions are the best technical solution to prevent email-based phishing attacks. They use advanced behavioral analysis to detect and prevent even the most sophisticated email attacks and provide additional training to users with in-line prompts and warning banners.
TitanHQ’s PhishTitan service is an ICES solution that provides effective protection against phishing, account compromise, CEO fraud, business email compromise and more. By leveraging this service, teams can rapidly improve their resilience against email phishing attacks. Get a demo of PhishTitan today.



