50 Phishing Stats You Should Know In 2025
We’ve cast our net for the latest phishing statistics to help you keep up to date on one of the largest threats your organization is facing.

Social engineering attacks are one of the most prevalent, and dangerous, types of cybercrime that organizations around the world are currently facing – but don’t take our word for it.
We’ve pulled together the most recent phishing statistics from around the world to help illustrate the breadth and severity of this threat. These stats come from third-party surveys and reports, and we’ll be updating them as new research emerges to help you stay on top of the latest figures.
The Frequency Of Phishing Attacks
According to recent research from IRONSCALES, 81% of organizations around the world have experienced an increase in email phishing attacks since March 2020, and a recent study by APWG observed a record number of phishing attacks in Q3 2022. But despite the very real threat that phishing poses to businesses today, almost 1 in 5 organizations only deliver phishing awareness training to their employees once per year. This lack of awareness is a large contributing factor to the fact that social engineering—attacks that manipulate the user into giving information to a cybercriminal—remains the threat type most likely to cause a data breach. In fact, according to Verizon’s 2022 DBIR, 82% of data breaches involve a human element, including phishing and the use of stolen credentials.
This figure is supported by further research conducted by the FBI’s Internet Crime Complaint Center (IC3), whose most recent Internet Crime Report found that phishing, including vishing, SMiShing and pharming is the most prevalent threat in the US, with 323,972 victims—up 34% compared to the previous year. This was followed by non-payment/non-delivery (82,478 victims), personal data breach (51,829 victims), identity theft (51,629 victims), and extortion (39,360 victims).
During these attacks, we’re increasingly seeing malicious data breaches being caused by stolen credentials. According to IBM, one in five companies that suffer a malicious data breach is infiltrated due to lost or stolen credentials, while 17% are breached via a direct phishing attack.
Phishing Delivery Methods
While the majority of social engineering attacks are delivered by email, one-third of IT professionals have experienced an increase in social engineering delivered via other communication platforms in recent years. These include video conferencing platforms (44%), workforce messaging platforms (40%), cloud-based file-sharing platforms (40%), and SMS (36%). As a result of this, we’re increasingly seeing email security providers shifting from traditional Secure Email Gateways, which block inbound threats, to providing security against outbound and internal threats, with integrations with popular messaging apps such as Microsoft Teams and Slack.
Email remains the number one method by which attackers phish their victims, and many of those attacks start with a “bait” or “reconnaissance” email. Bait emails serve two purposes: they verify the existence of the victim’s email account, and they attempt to gather more information about a victim, which a cybercriminal can use to carry out more targeted attacks in the future. The more the attacker knows about their victim, the more likely they are to manipulate that victim into trusting them. 91% of bait emails are sent via a Gmail account, with just 9% coming from other sending domains. This is likely because:
- Holding the second largest email client market share, Google’s email service is very popular and considered highly reputable
- Gmail accounts are quick and free to set up
- Gmail offers “read receipts”, which tell the actors when a victim opens their message, even if they don’t reply
But email and direct messaging apps aren’t the only way that threat actors phish their victims. In Q3 2022, APWG detected 415,630 unique phishing websites, which trick users into thinking they’re entering their credentials or payment details into a legitimate site, when actually that data is being harvested by a threat actor.
How People Are Getting Hooked
According to the results of Terranova Security’s 2022 Gone Phishing Tournament, 7% of all employees are likely to click on phishing email links. While this shows a huge improvement over the previous year’s report, in which almost 20% clicked on a phishing link, many of those who click still go on to follow through on further requests for sensitive information, such as entering credentials into a phishing webpage.
Subject Lines
According to research from KnowBe4, the most common subject lines to real-life phishing emails in Q3 of 2022 were as follows:
- Equipment and Software Update
- Mail Notification: You have 5 Encrypted Messages
- Amazon: Amazon – delayed shipping
- Google: Password Expiration Notice
- Action required: Your payment was declined
- Wells Fargo: Transfer Completed
- DocuSign: Please review and sign your document
- IT: IT Satisfaction Survey
- Zoom: [[manager_name]] has sent you a message via Zoom Message Portal
- Microsoft: Microsoft account security code
From these subject lines, we can clearly see that bad actors have been capitalizing on two main areas:
- People trust emails coming from reputable brands whose services they are using.
- Many organizations around the world have embraced a remote or hybrid way of working, and are using cloud technologies for important communications and sharing sensitive data remotely.
Attachments
According to one recent study, attachments are the third most common type of phishing attack, after a link embedded in the email content, and domain spoofing.
A recent Threat Report from ESET found that the most common types of malicious files attached to phishing emails are as follows:
- Windows executables (47%)
- Script files (23%)
- Office documents (19%)
- PDF documents (6%)
- Shortcuts (4%)
Brand Impersonation
According to Check Point, Yahoo is currently the most impersonated brand globally when it comes to brand phishing attempts, with 20% of all phishing attempts claiming to be from Yahoo and often offering large sums of prize money to the recipient. Yahoo is followed by DHL (18%), Microsoft (11%), and Google (5.8%).
The same report indicates that brand impersonation incidents are largely associated with brands in the technology sector, followed by shipping and social networks. These are all services largely carried out online, so users would expect to receive email communications from providers in these industries—making them less likely to question an attack.
Internal Threats
We often imagine the bad actor to be a hoody-wearing figure, cloaked in shadows, perhaps sporting a Guy Fawkes (or V for Vendetta) mask for added suspicion. However, this often isn’t the case at all.
According to research from accountancy firm BDO, around half of the frauds reported by respondents came from external parties, but an alarming 34% of business owners said that the fraudulent activities had “involved collusion” between their employees and bad actors. Even more shockingly, 21% said that their own employees had been behind the fraud.
Who The Victims Are
We’re all familiar with the fear-inducing headlines that scream news of nation-state-sponsored attacks against high-profile businesses, which lose millions or even billions of dollars to cybercriminals. However, small and mid-sized businesses are just as at risk of a cyberattack as large enterprises are, and they often don’t have the infrastructure or resources to defend themselves properly against attacks. Consider them “low-hanging fruit” for attackers.
BDO’s research found that six out of ten mid-sized businesses in the UK have been hit by fraud, suffering average losses of 245,000 pounds, and nearly 40% of all companies surveyed said they’d experienced increased fraud attempts compared to the previous year.
So we know that organizations of all sizes are under threat of falling victim to social engineering, but are any particular industries more at risk? Well, reports of social engineering incidents are highest in the Professional Services, Finance, Mining and Utilities, Manufacturing, and Public Administration sectors respectively. In terms of actual breaches suffered, the data looks a little different. Professional Services still takes the lead, followed by Finance, Mining and Utilities, and Healthcare, with Public Administration and Retail coming in joint fifth.
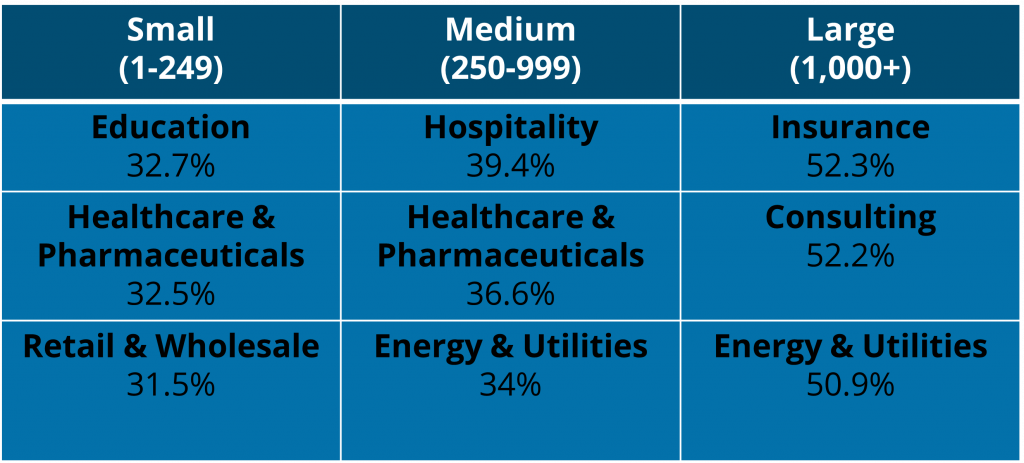
KnowBe4’s most recent Phishing By Industry Benchmarking Report found that the top industries at risk vary according to company size, but also reflect that education, hospitality, and insurance are among the most targeted industries, alongside healthcare, consulting, retail, and energy.
The same report found that among smaller organizations (1-249 employees), the industry least prone to phishing attacks is banking; among mid-sied organizations (250-999 employees), it’s government; among large organizations (1,000+ employees), it’s hospitality. However, even among these sectors, untrained users are still vulnerable to phishing attacks.
Finally, IBM found that the healthcare industry, though not always right at the top of the “most breached” lists, suffers the most in terms of the cost of a breach.
The Impact Of A Phishing Attack
Phishing attacks can be devastating to organizations that fall victim to them, in more ways than one. Let’s start by exploring the financial implications of falling for a lure.
The Financial Cost Of A Breach
According to IBM, the average cost of a data breach is 4.35 million dollars. This is higher than their figure from the previous year, and indicates that data breaches are becoming more financially dangerous. The majority of that cost is split between detecting and escalating the breach, and the cost of lost business. IBM’s study also shows a growing chasm in terms of the cost of a breach between organizations with more advanced security processes, such as incident response teams, and those with less processes in place. This means that, though costs are significantly lower for those with a formal security architecture in place, a data breach can cause irreparable damage to organizations without such protection.
IC3 found that social engineering scams are not only the most common but among the most costly: BEC attacks caused U.S. organizations to suffer an adjusted loss of around 2.4 billion dollars in their last study.
Those are some pretty big figures to get your head around, so let’s take it down to a per-business level: according to APWG, the average BEC wire transfer attempt requested in Q3 of 2022 was for $93,881.
The bottom line? Social engineering attacks are expensive, and this cost is only increasing.
The Consequences Of A Breach
The cost of a successful phishing attack can be broken down into the following categories:
- User downtime
- Remediation time
- Damage to reputation
- Loss of intellectual property
- Direct monetary losses
- Compliance fines
- Response and remediation costs
- Loss of revenue and customers
- Legal fees
However, financial loss isn’t the only impact that a phishing attack can have on your organization. A successful attack can also lead to:
- Lost data
- Compromised accounts or credentials
- Reputational damage
- Malware infections, including ransomware
Data loss is a key consequence of a successful phishing attempt, but what exactly does that entail? According to Verizon, the following are the top types of data that are compromised in a social engineering attack:
- Credentials, such as usernames and passwords (63%).
- Internal data, such as sales figures (32%).
- Personal data, such as addresses and phone numbers (24%).
Current Phishing Trends
The last few years have seen some massive changes to the way we work, from migration to a hybrid workplace, to rapid digital transformation, to an increase in the use of AI technologies. As organizations continue to embrace these ways of working, we’re seeing many of the attacks that were catalyzed by the COVID-19 pandemic and the shift to remote work continue.
Microsoft’s New Future of Work report found that 80% of security professionals have experienced an increase in security threats since shifting to remote work. Of this 80%, 62% say that phishing campaigns have increased more than any other type of threat.
As hybrid and remote workers continue to rely on digital forms of communication and instant messaging apps to collaborate, we can only expect these trends to persist.
How Can You Protect Your Business Against Phishing Attacks?
Unfortunately, there isn’t a single silver bullet solution to email security. We recommend taking a multi-layered approach to your phishing defense, by implementing a range of both technical and human-centric solutions.
Secure Email Gateway
Secure Email Gateways (SEGs) monitor your employees’ inbound and outbound emails, scanning them for malicious content. If the SEG detects any spam, phishing, or malware threats, it quarantines or blocks the email so that it never reaches its intended recipient.
However, while SEGs are very effective at blocking spam and traditional phishing attempts, sophisticated spear-phishing attacks are able to evade them by impersonating known trusted senders. To defend your data against internal threats, you need to implement a solution that protects each user at an individual level.
Cloud Email Security
Cloud email security solutions, also known as “post-delivery” email security, sit within your email network itself and monitor all inbound, outbound, and internal communications for malicious content. Cloud email solutions use AI and machine learning to analyze each individual employee’s communication patterns, then scan their email comms—and, in some cases, their communications via instant messaging apps like Slack or Teams—for anomalous behavior and malicious content. This enables the solution to detect more targeted and personalized spear-phishing attempts.
Security Awareness Training
Your employees are the heart of your organization, and they should also be a critical part of your cybersecurity defense strategy. Security awareness training platforms and phishing awareness training and simulation platforms deliver a program of engaging materials, combined with simulated phishing campaigns, to transform your employees from potential targets into a robust line of defense against social engineering attacks.
A strong training program can have a huge impact on the way in which your employees respond to phishing attempts. A recent report from Cofense (formerly PhishMe) found that employees who have completed a security awareness training program are far more likely to report a suspicious email than those who haven’t, greatly reducing the dwell time of a phishing email—i.e. the time taken to detect and remediate an attack.
Cofense’s study, which analyzed millions of results from their own simulated phishing campaigns, found that 82% of trained employees reported a simulated phish within an hour of receiving it, 52% reported it within 5 minutes, and 19% within 30 seconds.
The success of awareness training is further supported by research from KnowBe4, which found that, after completing one year of phishing awareness training, the average improvement rate across all industries and organization sizes was 85%.
Want to find out more about how you can protect your employees’ inboxes? Check out our buyers’ guides to the top security solutions that will help you defend against phishing attacks:



