Microsoft Teams Security: How Safe Is Teams For Your Business?
Teams is the market leading collaboration and video conferencing app worldwide. But how secure is it for your business?

Data is at the heart of every organization, so it’s crucial that the tools we use in the workplace keep our data secure and protect its integrity. And that includes the tools that we use for collaboration and communication. These two Cs are key to a team’s success; from detailed planning sessions to watercooler chats, we communicate to share ideas, offer support and grow as a business.
In 2020, millions of organizations around the world had to make rapid changes to their business architecture and the way they work to be able to support employees working remotely. As a result of this, a number of existing and emerging collaboration and video conferencing tools became extremely popular in the workplace—and as businesses continue to embrace the idea of a hybrid remote office, we can expect this popularity to be maintained. Microsoft are currently at the forefront of the market, followed by Cisco, Google, and Slack. Since launching in 2017, Teams has become Microsoft’s fastest-growing app. Today, Teams has 115 million daily active users, according to CEO Satya Nadella – that’s almost 50% more than recorded before the first major peak in the Coronavirus pandemic catalyzed the shift to remote and hybrid work.
Teams is a staple in Microsoft’s portfolio of Office 365 cloud applications. It integrates seamlessly with SharePoint, OneDrive and Outlook to offer robust file-sharing capabilities, as well as a strong instant messaging and video conferencing feature that allows up to 300 people per meeting.
All of this had led to Teams generally being accepted as the number one collaboration and video conferencing app. But with so many people relying on it worldwide, how secure is Microsoft Teams?
How Secure Is Microsoft Teams?
Microsoft classifies all of its Office 365 products into one of four compliance categories: A, B, C and D. Teams sits in category C, which means that security compliance commitments are enabled by default. Being in this category, Teams is compliant with a range of regulatory security standards, including ISO 27001, ISO 27018 and HIPAA Business.
Teams utilizes a number of security features to be able to meet these compliance requirements, including team-wide and organization-wide two-factor authentication and single sign-on, which admins can enable through Active Directory. This means that account security isn’t tied to password or device security, which is particularly important for workforces with employees using the app on their own personal mobile devices.
Active Directory also allows Teams to encrypt all data in transit and at rest to protect it from unauthorized viewing, and files stored in SharePoint and OneNote are secured with encryption protocols delivered via the two apps respectively. And this brings us on to our next point: data storage in Teams.
Every piece of data that you send via Teams, be it a file or instant message, is stored and backed up in Azure. Azure is delivered through data centers in 54 global regions, which allows Microsoft to store Teams data based on each organization’s region. This means that all data is stored in compliance with the data security regulations of the region that each organization is operating in.
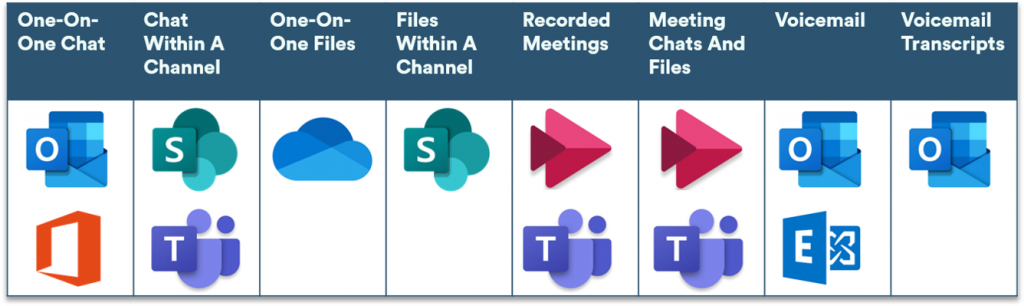
Files are stored in SharePoint or OneDrive for Business, meetings are stored in Stream, voicemails are stored in both Exchange and the user’s inbox, and chat messages are stored via eDiscovery in Exchange Online and in a hidden file within the user’s mailbox.
Finally, Teams automatically assigns one of two security levels to users, based on their role within the Team. Owners are users who create a group or Team. Members include anyone else who is added to the Team by the Owner. By default, Owners can restrict the actions of Members, including what content they’re allowed to view, whether they can create channels, and whether they can add new Members. This gives Owners a granular level of control over how data is shared in the groups they create—they’re basically an administrator for the team. By default, all users with an Exchange Online mailbox have the permissions required to create a Team and become an Owner. However, IT admins are able to delegate team creation and management rights to certain user groups, which gives them tighter control over the creation of new teams.
So, Teams has a variety of built-in security features which, thanks to Active Directory, admins can easily configure to meet the needs of their organization. But, like any other collaboration tool, it isn’t completely hackproof.
Data Breaches Within Teams
Access management vendor CyberArk recently discovered a subdomain takeover vulnerability within Teams that allowed potential attackers to use a malicious GIF to take over user accounts. The method of attack exploited the way in which Teams uses access tokens to allow users to view images, and acted in a similar way to a worm virus in that it could be spread automatically. It meant that the attacker could send their victim a malicious GIF and gain access to their account as soon as the victim viewed the image, without them having to share it or download anything.
Because the GIF could also be sent to multiple Teams, attackers could gain control over multiple accounts quickly and easily. With this account access, attackers could gather sensitive and confidential information such as login credentials, meeting information and competitive data, and use it to cause both financial and reputational damage to the organization. CyberArk’s report on their findings called it “a nightmare from a security perspective”.
After CyberArk disclosed the vulnerability, Microsoft patched it before any bad actors could exploit it. However, this highlights the need for an organization to have strict security protocols in place before rolling out Teams.
Microsoft Teams Best Practices
First things first, let’s start with the basics. You need to make sure that only authorized users can access your organization’s Teams platform. Notice that I said “users” and not “employees”—that’s because this rule extends to partners and clients that you might want to give temporary access to a specific Team whilst working on a project.
To take control of this access, there are three things you need to do:
- Make sure that you enable Teams’ two-factor authentication (2FA) through Active Directory. You can visit Microsoft’s documentation pages to find detailed instructions on how to set up 2FA for Office 365 apps.
- Enforce least-privilege access so that users can only access the resources that they absolutely need to be able to perform their role. This means that if an attacker compromises an employee account, they’ll only be able to access a restricted amount of data, not that of the entire organization.
- Prevent file download to unmanaged devices. This is particularly important for organizations with a large number of remote employees who are using personal devices to access Teams and other workplace applications. Unmanaged personal devices don’t usually have the same tight security measures in place as corporate-issued or managed personal devices so, if they’re lost or stolen, an attacker could easily access any files downloaded to the device.
The Top Microsoft Teams Security Providers
As well as following best practices, there is a range of robust tools out there that you can use to bolster your Teams security. To find the best tool for your business, take a look at our guide to the top enterprise security tools for Slack and Microsoft Teams.
These solutions scan inbound files and content to protect users from malware, and they scan outbound content to prevent the unauthorized distribution of sensitive data.
Further Recommendations
No single security solution is bulletproof, so we always recommend that you implement layers of security to make it as difficult as possible for attackers to infiltrate your network. To further protect your Teams data against unauthorized access, you should consider deploying the following solutions:
Multi-Factor Authentication
Multi-factor authentication is a security protocol that requires users to provide two or more forms of identity verification before they’re allowed access to an account. Secondary methods of authentication could involve something the user knows, such as a PIN, something the user has, such as an authenticator app, or something the user is, which refers to biometric data such as a fingerprint. MFA ensures that attackers can’t access an account, even if they manage to crack or steal the account holder’s password. Although admins can enable two-factor authentication for Teams through Active Directory, this setting could be disabled if a bad actor were to compromise an admin’s account. For this reason, we recommend that any organization using Microsoft Teams implement a secure multi-factor authentication solution from a third-party provider.
Unified Endpoint Management (UEM)
Unified endpoint management solutions allow organizations to monitor and manage all PC and mobile devices connected to their network, including the applications installed on those devices. They combine traditional mobile device management (MDM) and client management tools (CMTs) to provide a single management interface for all connected endpoints.
The strongest UEM solutions provide useful analytics on device usage, including what apps are being used and why, to help the organization configure usage policies.
When choosing a UEM solution, the feature that you need to look out for here is application isolation capability, usually delivered via a digital workplace. This allows users to separate their workplace and personal applications and use both securely from one device.
Endpoint Protection
Endpoint protection solutions secure all of the devices connected to your corporate network against malware, spam, and phishing attempts. They often leverage both artificial and human threat intelligence to quickly detect and remediate advanced threats across endpoints, including threats within your Microsoft 365 environment — this will stop users from receiving and opening any malicious URLs or attachments in Teams, in the case that a bad actor does manage to gain access to a trusted user’s account.
There are a lot of endpoint protection solutions out there, so you need to make sure you’re looking for a solution that’s cloud-hosted and integrates easily with Microsoft Office 365.
Backup And Recovery
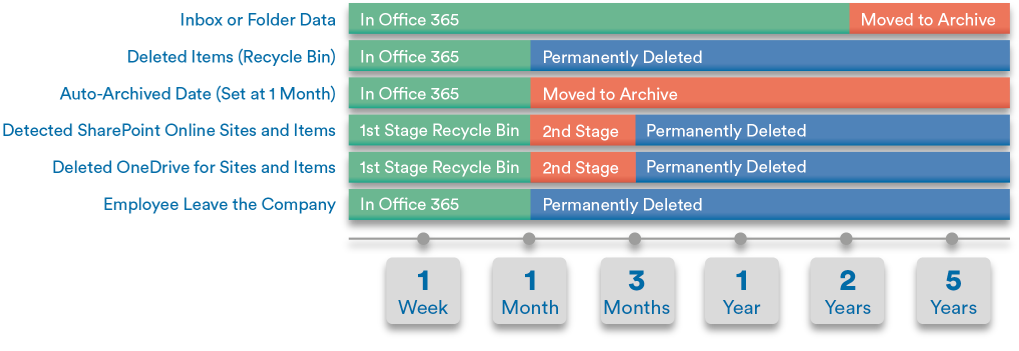
Although Microsoft backs up your Teams data to other areas of your Office 365 environment, it doesn’t secure it there forever. In fact, Office 365 only protects data for an average of 30-90 days, which can be hugely problematic if any of your accounts *are* compromised or you experience a technology failure that results in data loss. Unfortunately, Microsoft Office 365 accounts are a common target for attackers because they allow the attack, such as ransomware, to spread laterally (and easily) to other accounts and users within the organization.
For this reason, we recommend that you implement a strong backup and recovery solution to make sure that your data is always secure, and that you can easily restore it should you need to (touch wood).
Summary
As collaboration applications go, Microsoft Teams is one of the most secure ones out there. But attackers are always looking for new, sophisticated ways to access even the most well-protected systems.
Teams can hold a lot of valuable company information, both in terms of the files that we share and the secrets stored within personal one-on-one chats. In order to protect this data, it’s crucial that you follow the best practices outlined in this article and, for a further layer of protection, consider implementing a strong multi-factor authentication, endpoint protection, UEM and backup and recovery solution.
There are a lot of solutions to choose from when it comes to these market areas, so it’s important that you consider your organization’s needs when looking for a product to invest in, and weigh these against each solution’s features. To help you get started, we’ve put together guides to the top solutions currently on the market:



