
50 Endpoint Security Stats You Should Know In 2025
We’ve collated the latest endpoint security statistics to help you keep up to date on one of the most important security topics facing the modern workplace.

Each of your company’s endpoints is a doorway through which your employees access your corporate data. Today’s workplace comprises a combination of office-based, remote and hybrid workers who are increasingly using their personal devices in order to work from anywhere. However, there are two sides to every coin: though they increase employee flexibility, “bring your own device” (BYOD) work fleets pose some serious security risks without the proper protection in place.
We’ve collected the most recent endpoint security statistics from around the world to help illustrate the need for a robust security architecture surrounding your network’s endpoints. These stats come from third-party surveys and reports, and we’ll be updating them as new research emerges to help you stay on top of the latest figures.
The Frequency Of Endpoint Attacks
According to a study by the Ponemon Institute, 68% of organizations have experienced one or more endpoint attacks that successfully compromised data and/or their IT infrastructure. The same report found that 68% of IT professionals found that the frequency of endpoint attacks had increased since the year before.
Further research by Ponemon found attacks on endpoints to be some of the most prevalent that respondents had experienced, with 81% of businesses experiencing an attack involving some form of malware, and 28% experiencing attacks involving compromised or stolen devices.
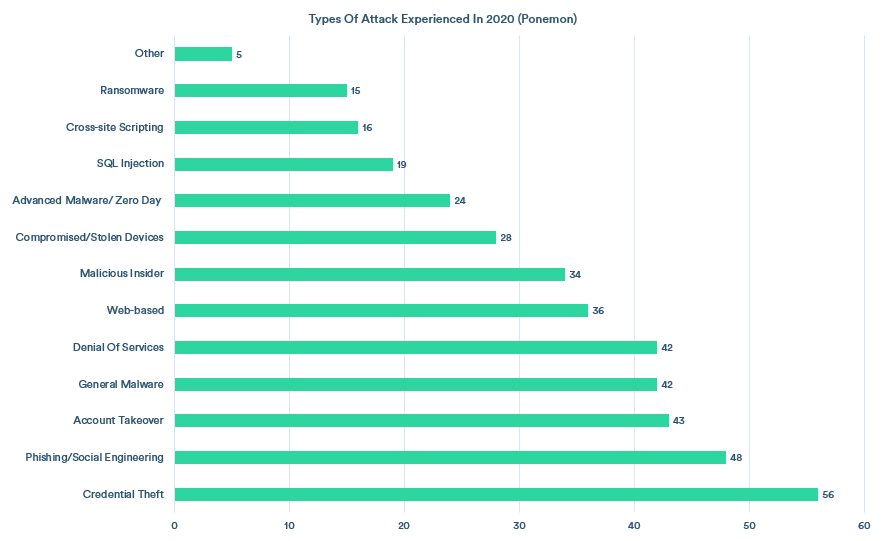
Ransomware is one of the most common and most dangerous types of malware currently in circulation. Once downloaded to the victim’s device, the malware holds corporate data hostage by locking users out of it or encrypting it until the target organization pays a ransom. 53% of organizations were hit by a successful ransomware attack in 2021, and around 23% of those were hit more than once.
And, unfortunately, this figure shows us that ransomware is on the rise. Recent research by SonicWall reported that recorded ransomware incidents last year represented a staggering 148% year-on-year increase over 2020. A further study by Check Point also reported a rise, finding that, throughout 2021, the weekly average of ransomware attacks targeting corporate networks increased by 50% compared to 2020.
With that in mind, it comes as little surprise that 69% of CISOs expect to fact at least one ransomware attack in 2022.
Endpoint Attack Methods
Malware is one of the most common ways by which attackers target endpoints, which can be installed in a number of ways on the target’s device. Verizon found the use of password dumpers, which enable attackers to steal the credentials stored on a compromised device, to be the most common type of malware breach, involved in around 40% of breaches. Password dumpers are followed by capturing application data and ransomware respectively.
The same report found that Windows applications and Office documents were among the top filetypes within which malware is contained, and that email and web are the preferred malware delivery methods.
Research from Webroot further indicates that 83% of malware threats are stored in one of four locations: %temp%, %appdata%, %cache% and %desktop%.
Malware can also be installed via “juice jacking”, which is a method that involves modifying USB ports in order to install malware onto the victim’s device. These ports are often disguised as free chargers in public spaces. This method of installation is one for organizations with a large number of remote workers to watch out for, or workers who regularly travel as a part of their role. 79% of people travelling for business have connected their devices to a public USB port or charging station – unknowingly opening the door for a potential attacker.
However, malware isn’t the only threat to your organization’s endpoints. “SIM swapping” is a type of cybercrime that involves the attacker calling up their target’s mobile phone provider whilst impersonating that target, and asking them to transfer their target’s phone number to one owned by themselves. This enables the attacker to redirect all of their target’s calls and SMS messages. SIM swapping attacks on mobile endpoints have doubled year-on-year since 2016, as the number of people using personal cell phones for work has increased.
Ransomware
Ransomware is one of the most prevalent forms of malware. According to research from Sophos, ransomware is most likely (29%) to enter an organization via file download or an email with a malicious link. This phishing delivery technique is followed by remote attacks on servers, accounting for 21% of ransomware attacks, and emails with malicious attachments, which account for 16% of attacks.
These figures are backed up by recent research from SonicWall, which reports that Ryuk ransomware, often distributed via TrickBot or Emotet phishing campaigns, is responsible for a third of ransomware attacks.
But where does your data go once the ransomware is installed?
Well, 59% of ransomware attacks where the data is encrypted involve data in the public cloud, such as Office 365 or Amazon Web Services (AWS). This is both in terms of where the data is stolen from, and how the attacker uses it. At attacker typically sends stolen data to a legitimate cloud storage service, which makes the activity more difficult to pick up. Google Drive, Amazon S3 and Mega.nz are the most common cloud storage services for storing exfiltrated data.
Vulnerabilities, Patching And Updates
On average, 80% of successful breaches are new or unknown zero-day attacks. These attacks either involve new or evolved malware variants that infiltrate a system unrecognized, or the exploitation of undisclosed vulnerabilities.
It can be difficult to keep your vulnerabilities patched. The same study found that it takes an average of 97 days to apply, test and deploy a patch, and that 40% of organizations prefer to take their time in testing and rolling out patches in order to avoid issues later on.
The increase in remote workers since the beginning of 2020 has meant that organizations have had a whole new range of mobile devices to monitor and manage – including administering patches and ensuring the operating systems are kept up to date.
One in three US employees (33%) use a personal computer and smartphone to work remotely, while only 17% use a corporate-issued computer and smartphone.
According to the results of a Ponemon Institute survey, 55% of professionals consider smartphones to be amongst their most vulnerable endpoints. 50% considered laptops to be particularly vulnerable, 24% considered tablets and 48% answered with other mobile devices. Only 34% considered desktops to be amongst their most vulnerable endpoints.
The challenges involved in patching and updating operating systems across a remote workforce mean that, across managed enterprise Android devices, only 21.2% of updates are made immediately; 18.2% are deferred, 12.2% are windowed, and an alarming 48.5% of updates aren’t managed at all.
But why is administering patches and updates so important? Well, older, unpatched devices are much more vulnerable to malicious applications than new devices with the patches for these exploits deployed. Malicious mobile code written into applications can enable attackers to access the user’s voice and text messages and emails, as well as access their camera, location information and monitor their keystrokes. A recent report from Webroot found that more than 40% of Android devices are using an OS version older than v9. This makes them much more susceptible to attacks, and should be a cause for concern for BYOD workforces.
Considering these statistics, it’s no wonder, then, that 67% of IT professionals believe the use of BYOD devices during the COVID-19 pandemic to have decreased their organization’s security posture, and that 71% are concerned that remote workers are putting their organization at risk of a data breach.
Who The Victims Are
Organizations with large numbers of remote workers or BYOD devices are at the most risk of experiencing an endpoint attack. Personal consumer devices are twice as likely to become infected with malware than their business counterparts.
However, despite the increase in security risks associated with remote working, only 47% of organizations monitor their networks 24/7, and only 50% encrypt sensitive data that’s stored on devices. Additionally, less than half of businesses both monitor their network and protect company-owned devices with up to date antivirus software, device encryption and firewalls.
When it comes to ransomware, we often see headlines screaming news of multi-million or -billion dollar attacks against international enterprises. However, there’s really little difference in attack rate in relation to an organization’s size: 47% of SMBs (100-1,000 employees) have experienced a ransomware attack, compared to 54% of larger organizations (1,001-5,000 employees). This is because cybercriminals often view smaller companies as easy targets or “low-hanging fruit”, due to their lack of dedicated security resources and infrastructure.
Additionally, public sector organizations are less likely to be affected by ransomware than those in the private sector. The most affected sector is the media, leisure and entertainment industry, within which 60% of organizations have experienced a ransomware attack. This is followed by IT, technology and telecoms (56%), energy and utilities (55%), and professional services (50%).
Another study found that, in by the end of 2021, the education & research, government & military, communication, MSP and healthcare industries were the most commonly targeted by ransomware.
The Cost Of An Endpoint Breach
According to IBM, the average data breach costs 4.27 million dollars. Ransomware attacks and malicious attacks that destroy or wipe data in a destructive way cost an average of 4.62 million and 4.69 million dollars respectively, while the cost of a successful endpoint attack has increased from 7.1 million dollars to 8.94 million.
According to research by Coveware, the average payout of ransomware attacks stayed fairly consistent between Q2 and Q3 2021, yet the median payout doubled. This could be due to the fact that attackers are avoiding larger targets that might result in a national political or law enforcement response, and are instead targeting mid-market organizations.
In addition to the financial cost of a ransomware attack comes the (increasingly common) consequence of data loss: over 80% of ransomware attacks in Q3 2021 involved a threat to exfiltrate data. When data is at the heart of every organizations, it’s no wonder that—despite warnings against it from law enforcement agencies—an increasing number of organizations are choosing to pay the ransom: In Q3, 47.8% of companies chose to pay; this increased to 59.6% in Q4.
Downtime is another huge cost of ransomware attacks; in Q4 of 2020, the average company affected by ransomware experienced approximately 21 days of downtime.
When responding to a ransomware attack, it’s always safer to try and recover your data from backups than to pay the attacker’s ransom, if you have the backups available. Sophos’ study found that more than twice as many (56%) companies managed to recover their data from backups than by paying the ransom (26%). And paying the ransom doesn’t always mean that you’ll get your data back – you are dealing with a cybercriminal, after all. A further 1% paid the ransom but didn’t get it back.
On top of this, Sophos’ research found that paying the ransom doubles the cost of dealing with a ransomware attack.
This cost averages 761,106 US dollars globally; 505,827 dollars for companies with 100-1,000 employees; and 981,140 dollars for companies with 1,000-5,000 employees.
So you now know not to pay the ransom, but if you’re looking for more advice on how to recover from a ransomware attack, you should check out our guide to ransomware recovery.
Current Endpoint Security Trends
Currently, around 58% of organizations around the world’s workforces “telework”. Remote working enables employee flexibility, but it also presents a number of security challenges. When asked which of these security risks they’re most concerned about, respondents of a Ponemon survey answered:
- Lack of physical security in the workspace (47%)
- Risk of malware infection (32%)
- Criminals gaining control over remote devices to steal sensitive data (24%)
- Securing external comms (23%)
- Securing the network (20%)
- Criminals leveraging devices to gain network access (17%)
- Phishing and social engineering attacks (15%)
- Devices being lost or stolen (12%)
- Securing external access to internal resources (8%)
As we can see, four of the top nine concerns involve attacks on endpoints. And this comes as no surprise, as the same survey found that, since the start of the pandemic, 51% of organizations say that exploits and malware have evaded their intrusion detection systems, and 49% says that exploits and malware have evaded their antivirus software.
How Can You Protect Your Business’ Endpoints?
One-third of small businesses in the UK and US use free, consumer-grade cybersecurity, and 23% don’t use any endpoint security platform at all.
Endpoint attacks are on the rise, and it isn’t enough to just hope that your organization won’t fall victim to one. Unfortunately, as the number of attacks increases, so does their sophistication. It’s for this reason that 51% of IT professionals consider endpoint attacks to be successful because their endpoint security solutions aren’t effective enough at detecting threats.
It can be challenging to find the right security solution for your organization in a market that’s crowded with noise – but that’s where Expert Insights comes in. We’ve put together a series of guides to the top solutions that will defend your endpoints against viruses, malware and malicious applications, and help you mitigate the consequences of ransomware attacks:



