
MFA Bypass Attacks: How Do They Work, And How Can You Avoid Them?
MFA bypass – which includes MFA fatigue, token theft and Machine-in-the-Middle attacks – is a major threat for security teams. How do MFA bypass attacks work, and how can you ensure that you are protected?

Implementing multi-factor authentication (MFA) is a simple and effective process that organizations can use to reduce their risk of security breach. In fact, research from Microsoft has found that taking this one simple step can stop 99.9% of attacks on your account.
In a recent interview with Expert Insights, Alex Weinert, the Director of Identity Security at Microsoft, said that organizations should “look at multi-factor authentication as the baseline,” – i.e., the absolute minimum level of security put in place to protect account access.
Multi-factor authentication requires users to provide an additional “factor” of identity verification when accessing their accounts or devices. Traditionally, users have only need to provide one factor: either a password or a PIN. With MFA in place, users must provide two or more factors, which can include a verification code from a trusted device, or a biometric, such as a fingerprint scan. You can read more about how multi-factor authentication works here.
MFA has become critical due to the inherent weakness of using passwords alone. Passwords are often reused and easy to compromise in phishing and malware attacks, leaving user accounts exposed to cybercriminals. With MFA in place, these attacks become much, much more difficult to execute.
But it’s not impossible. As MFA adoption slowly increases, cybercriminals have found new, highly effective workarounds, which have become known in the industry as “MFA bypass” attacks.
What Are MFA Bypass Attacks?
MFA bypass attacks can be defined as essentially any attempt used by cybercriminals to avoid or circumvent multi-factor authentication to gain access to user accounts. According to Microsoft’s Director of Identity Security, there are three dominant forms of MFA bypass attacks commonly seen today: MFA fatigue, token theft, and Machine-in-the-Middle attacks.
Let’s take a look at how each of these attacks work in more detail.
1) MFA Fatigue
MFA fatigue is one of the most common and high-profile ways to bypass MFA. It is seen as a form of social engineering, as it involves cybercriminals manipulating users into giving them access to their accounts unwittingly.
The way MFA fatigue works is straightforward. MFA often requires end-users to make an action on a personal device to gain access to an account. For example, a pop-up may appear on a smartphone, or an email may be sent, which, when accepted, will then allow a user access.
However, if a cybercriminal is able to compromise a username and password, this means they can request access to the legitimate user over and over again, sending pop-up after pop-up, until the user gives in and accepts. As Alex Weinert puts it: “Attackers can just wear you down. They’ll call an employee over and over again, until finally they say, “Yes, just make the phone call stop!”
This can also extend to enterprise MFA solutions. In the recent high-profile Uber breach, an 18-year-old hacker was allegedly able to breach Uber’s internal systems and bypassing Duo, a leading MFA service reportedly used by Uber. First, the attacker was able to steal an Uber employee’s credentials through a malware attack. Then, he hit the MFA wall.
Duo ensures that only registered devices can be used to authenticate access. As reported by Kevin Beaumont on Twitter, the attacker was able to send multiple push notifications to the affected user, and eventually reached out to them over WhatsApp pretending to be from Uber’s IT support team. Eventually, the user accepted the request, giving the hacker access.
Similar forms of MFA fatigue attacks in the past year have been used to breach both Microsoft and Cisco.
2) Token Theft
Token theft is one of the most common forms of MFA bypass attacks. As Alex Weinert told Expert Insights:
“The dominant [form of MFA bypass] we worry about is token theft. The way multi-factor authentication protocols work is that, once you’ve been introduced to an application, it may place a session cookie on your machine that allows you to continue. If an attacker picks up that session cookie and moves it to another machine, all of the rules that were in place to get that cookie are irrelevant, and you have a problem.”
“And there are various types of cookies that can be stolen. So, attackers are looking at cookie theft as a way to bypass good security. So, endpoint protection actually becomes more important, because you’ve got to keep that malware off of your machine.”
Essentially, this attack involves cybercriminals scraping cookies, the session code used by web browsers to track users as they log-in to different web pages. Cookies are designed to reduce friction for users, meaning they don’t have to re-authenticate every time they access a different webpage in the same session. When these attacks are successful, this allows criminals to place these cookies into their own session, and thereby trick the browser into believing they are the authenticating user and bypassing MFA.
3) Machine-In-The-Middle Attacks
The third form of MFA bypass is Machine-in-the-Middle, or Adversary-in-the-Middle attacks. This is a form of phishing attack which is used to trick users into clicking a malicious link, giving cybercriminals access to machines while circumventing MFA controls.
Firstly, an attacker will trick a user into clicking on a malicious URL, directing the user to a malicious proxy server. Using this server, the attacker will then be able to intercept network traffic between the user’s computer and the real web server. This will then allow the attack to capture data from the user’s web session, including credentials, and MFA session cookies, allowing the execution of a token theft attack.
How To Avoid MFA Bypass Attacks
Over time, methods of MFA bypass are likely to become like weeds in an overgrown garden, or moles popping up in a retro arcade machine. When one is dealt with, more will appear, as cybercriminals strive to find ways to access valuable enterprise data.
There are ways for organizations to mitigate these attacks, but our first piece of advice is to ensure that your organization has MFA switched on. MFA adoption is growing – in 2017, adoption rates were at just 1%; in 2022, that number has risen to 25% – but that still means 75% of organizations still have no MFA protection in place.
If you don’t have MFA switched on, you will have bigger security vulnerabilities than those raised by MFA bypass attempts. As Weinert puts it: “Until you fix the MFA problem, you might as well not worry. Because it’s like you have the barn door open and you’re worrying about how good the lock is on the side door. It doesn’t matter.”
If you’d like to find out more about the MFA solutions currently on the market, you can read our guide to the top MFA solutions here. With that said, here are the security best practices to implement to avoid MFA bypass attacks:
Set Push Notification Limits
The first important step to avoiding MFA fatigue attacks it to set limits on the number of MFA push notifications that can be made before access is accepted into accounts, or to disallow the use of push notifications altogether as an authentication method. This is an important feature to look for in an enterprise MFA solution.
As covered, MFA fatigue attacks occur when an attacker is able to spam users with requests to give them access to accounts. By limiting the number of times these requests can be made, the likelihood of a fatigue attack being successful is reduced.
MFA solution providers will have a default number of authentication attempts that can be made before the attacker is locked out is locked out for good. In the case of Duo, the platform reportedly bypassed during the Uber attack, the default limit is ten attempts. It’s unclear if Uber was using the default setting, but setting a limit is an important way to prevent MFA bypass.
Some security experts have even recommended disabling MFA push requests altogether. This is an effective way of preventing push notification spam, as users will need to open their authenticator application manually – which often involves entering a PIN or scanning their fingerprint – each time they wish to authenticate a login attempt.
Switch On Number Matching
Number matching is a security feature designed to prevent MFA bypass by ensuring that only a legitimate user requesting access is able to authenticate their identity. The way it works is straightforward: when a user needs to approve a sign-in attempt, they’ll be given a code on their browser, which they must then input onto their mobile device to allow the authentication.
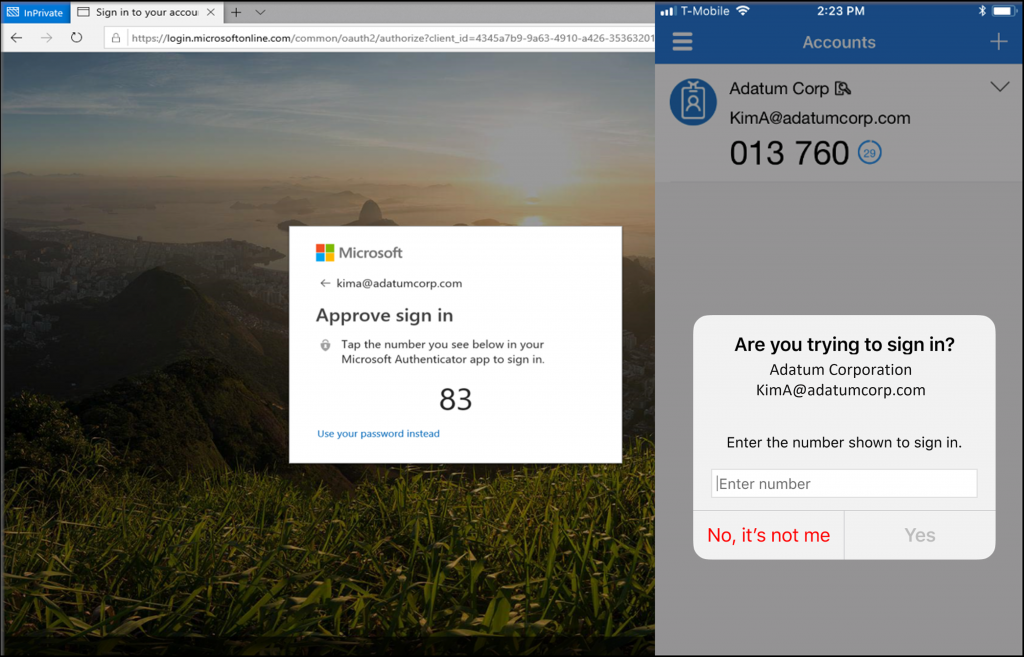
This is highly effective, as it means that a malicious third party who has compromised user credentials would need to contact the end user to ask them to input these numbers into their authenticator app, something that should immediately raise alarm bells.
Number matching is available through Duo with a feature known as “Verified Push”, and through Okta. Microsoft also offers number matching and is planning to enable it as a default for all Azure Active Directory tenants.
Awareness Training
The ways in which attackers both gain access to passwords and execute MFA fatigue attacks rely on a common denominator: human error. Users don’t often consider security, authenticator apps, or session tokens. They simply want to log on and get their work for the day done. Cybercriminals exploit this lack of awareness to trick users with attacks designed to trick users into giving up their credentials.
Security awareness training can be an important way to help demonstrate to users the importance of good security hygiene. In the case of MFA fatigue attacks, awareness training be hugely significant: a user who knows about the risks of compromised accounts and phishing is unlikely to be fooled by spammed push notifications.
Of course, awareness training is not a silver bullet, and it’s still important to have strong technical security in place to protect users. But implementing engaging and effective training can be an important way to improve account security. You can read our guide to the top awareness training solutions here.
Consider FIDO Hardware Security Keys
While number matching and awareness training are important ways to prevent MFA bypass caused by fatigue or social engineering, they are not going to be an effective way to prevent session-based MFA or Machine-in-the-Middle attacks. Preventing these attacks requires a much more robust form of MFA to be implemented, often requiring the use of FIDO2 or hardware keys.
The FIDO project is an alliance between hundreds of global technology leaders, including Apple, Google, Microsoft and Meta, as well as leading authentication providers such as RSA and Yubico.
Together, they have developed a set of authentication standards based on public key cryptography for a method of authentication designed to be more secure than passwords and traditional forms of multi-factor authentication such as SMS OTPs, but also easy to manage and integrate with all service provides.
One of the key components of FIDO2 is WebAuthn, an API which secures user access by using registered devices as factors of authentication. This replaces password logins entirely with a secure alternative. Session tokens are no longer stored in the browser, and instead are stored locally on devices, reducing the risk of token theft as information is no longer stored in web browsers where it can be intercepted.
This technology is being rolled out steadily in consumer services, with Apple bringing Passkeys – a passwordless way to authenticate access built on the FIDO2 WebAuthn standard – into iOS 16. But it can also be used in corporate authentication processes, commonly with the use of hardware-based authentication tokens, such as Yubico’s YubiKey 5.
Using hardware tokens as a factor for multi-factor authentication is already highly secure and can help prevent MFA fatigue attempts, as attackers would need access to the physical token in order to gain access to accounts. Combining this with FIDO2 passwordless access is one of the most secure and effective ways to help prevent token-based and Machine-in-the-Middle MFA attacks. Vendors like Yubico can support both use cases.
It’s important to note that implementing full FIDO2 authentication with hardware keys can be expensive and highly complex, with some debate in the security industry as to whether it’s needed or ready for mass use. But there are some important security and ease-of-use benefits: with one key, users can securely access all of their accounts.
Read Next The Top 11 FIDO Authentication Solutions
Summary
MFA bypass attacks are expected to become increasingly common as adoption of multi-factor authentication increases. These attacks can range from the devious to the highly sophisticated, so it’s important to consider your security frameworks and the processes you have in place to protect against them.
For more on the best ways to prevent MFA Bypass, read our guide to the Top MFA Bypass solutions.



