
What Is The Difference Between 2FA And MFA?
What are multi-factor authentication (MFA) and two-factor authentication (2FA), and what’s the difference between them?

Multi-factor authentication (MFA) and two-factor authentication (2FA) are security protocols that protect accounts by verifying user identity. They are both ways of verifying that you are who you say you are, and that you have the right to access a specific account.
MFA and 2FA are an important obstacle between your sensitive data and malicious actors. According to Microsoft, MFA can block over 99.9% of account compromise attacks. Enforcing MFA on all users’ accounts is a good idea as it will reduce the chance of accounts being used to disseminate phishing mail and helps to prevent a compromised account granting lateral access to steal sensitive data.
What Are The Factors Of Authentication?
Before moving onto explaining how MFA is different to 2FA, it is worth, briefly, exploring what the different types of authentication factors are.
There are three broad categories of factor:
Knowledge
This type of factor relies on the authentic user knowing a piece of information that a non-authentic user does not. The best example of this is a password. With this secret piece of information, you are granted access to your account. Knowledge factors can, however, be shared or guessed, without the authentic user being aware of this compromise.
Possession
These factors verify identity by confirming that the person trying to login has access to something linked to the account owner. Usually, this is a hardware device like a security key, or a smartphone. A user might have an authentication notification sent to their cell phone. From here they can easily accept or reject the login attempt. While it is not impossible for an attacker to gain access to your mobile device, it is significantly more complex than gaining access through a password alone.
Inherence
This is the most secure type of factor. It verifies your identity using a biometric trait. This is most commonly achieved through fingerprint analysis or facial recognition. Most high-end smartphones have these sensors built-in, meaning that biometric authentication can be deployed widely. Increasingly, companies are incorporating more types of biometric analysis – even the way you type can be analyzed to confirm identity.
What Is 2FA?
2FA is a way of verifying a user’s identity by using only two factors of authentication. In other words, two different sources must confirm that you are who you say you are, before you are granted access to an account.
Common factors might be a password and an SMS-based one time passcode (OTP). You might have used this mode of 2FA when logging into a new account, or before making an online payment. Before you can gain access to your account, you will receive a passcode that you must enter into the browser, in order to verify your identity.
What Is MFA?
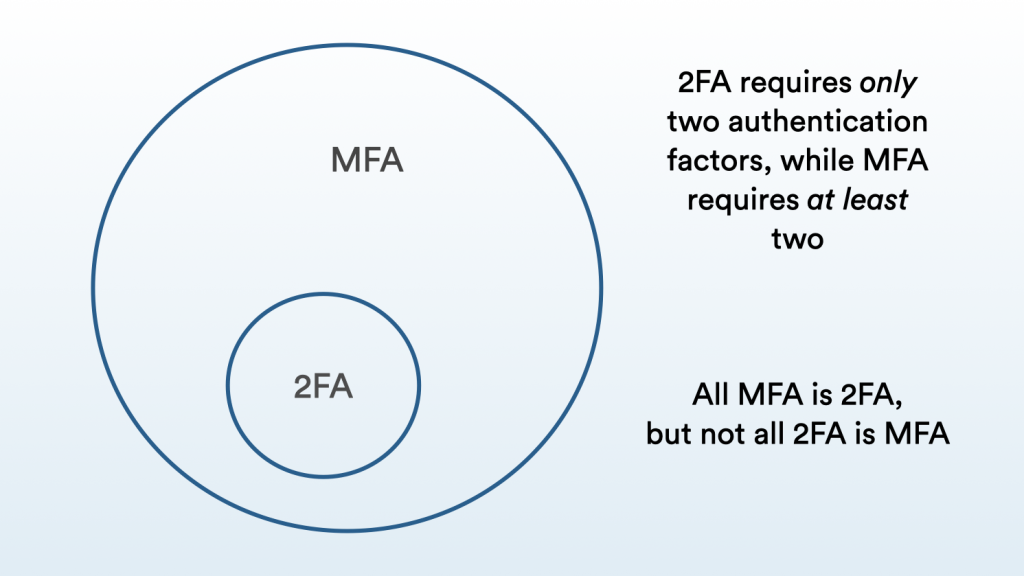
If two-factor authentication requires two identity confirmations, how many does multi-factor authentication require? MFA requires at least two. With this in mind, all MFA is 2FA, but not all 2FA is MFA.
MFA will use either pre-set or contextual information to decide whether a third authentication factor is required. Pre-set conditions might dictate that a higher level of authentication is required when accessing specific accounts, or particularly sensitive areas of a network. Personally identifiable information (PII), for example, might require a third authentication factor before being accessed. You might need to use MFA at the start of the week, but only 2FA when you login each morning. This ensures that identity has been recently verified, without impacting on an employee’s productivity.
MFA can also use contextual factors to make an informed decision of when MFA should be enforced. This is intelligent analysis that works behind the scenes to indicate if there is any reason to be suspicious about a user’s login. MFA that uses contextual factors to analyze login attempts and “step up” authentication is commonly known as “risk-based” or “adaptive” authentication.
What Are Contextual Factors?
Contextual (sometimes called behavioral) factors can build up a picture of a user’s behavior over time. This will then be used as a baseline to inform verification decisions. If a login attempt fits with “normal behavior”, there is no need to ask for a third verification method. If there is anything unusual or suspicious about the login, an additional factor will be required. The MFA solution then has more information to decide if a user is who they say they are, and if they should be granted access.
So, what are the different types of contextual factors?
Geo-based
By logging where in the world a user normally logs in from, your MFA solution can understand if your behavior is normal. If a user always logs in from their office in New York, the MFA solution can recognize this and allow it. If, however, a user logs in from a new location (such as a city in another country), there is a chance that a fraudulent user is attempting to gain access.
In this instance, the user will be asked to further verify their identity. If a third factor confirms their identity, they will be granted access. If they are unable to do this, their access will be denied. This ensures that if the user has legitimately travelled to a different location, they can gain access, while preventing fraudulent users from getting in.
For a more detailed explanation of how solutions use geo-based authentication, read our article on impossible travel logins here.
Time Based
As with the previous example, a user’s usual behavior can be logged to corroborate future logins. If a user usually logs in between the hours of 9:00 and 18:00 (i.e., their usual working day), a login attempt that occurs outside of this window can be flagged as suspicious.
This type of contextual factor can be a very good indicator of when a fraudulent attempt is being made. Attackers will often try to break in overnight as there are fewer staff to identify and respond to the breach. This type of context becomes more complicated for multinational organizations who operate in multiple time zones. Even if you know where a user is, and when they usually log in, they might have to work outside of normal hours for key meetings.
Device Based
Through logging IP addresses, MFA solutions can ensure that you are logging in from your own device. There are, of course, examples of when a new device will be used, however, keeping track of a user’s device is a quick way of identifying something suspicious.
This contextual factor allows for users who travel a lot for work to stay secure and productive. It does not matter that they’re in a different location geographically, as the device they are using remains consistent.
Does Your Business Need MFA?
In the complicated world of cybersecurity, this question has a simple answer. Yes. Or rather, you need some type of authentication further than your users’ standard username and password. While MFA is generally accepted as the most secure option, 2FA can be a very strong and secure solution too.
If your 2FA solution is configured correctly, it will add a very important layer of security to your accounts. If an opportunist hacker is looking for accounts to attack, having 2FA might be enough to ward them away, and pick on an easier target.
To ensure your 2FA solution is as effective as it can be, you want to ensure that password policies are complex enough that they cannot be guessed in a brute force attack. This is where an attacker repeatedly attempts to guess your password by making numerous attempts. Using non-standard characters, numbers, and longer passwords can make this attack less likely to succeed.
Using hardware keys or biometric factors will also ensure your accounts are as protected as they can be. These are physical devices that must be plugged in (or connected via NFC) at the time of logging in. This additional identity confirmation is often protected with FIDO 2 protocols, advanced encryption, and can even require biometric authentication to unlock the key.
MFA is generally more secure than 2FA, especially if contextual analysis is enabled. As this happens in the background, your users will be unaware that these checks are happening. This ensures that their workflow is not affected by this additional layer of security.
So, yes. You should have MFA, or at least 2FA, enabled on your accounts. It is a very simple solution to implement and engage with, but provides an impressive and significant pay off.
Summary
One way to think about the difference between 2FA and MFA is that MFA is an extension of 2FA.
2FA provides a strong layer of security that is essential in protecting your accounts from access by an unauthorized user. MFA builds an additional layer of security onto this; where 2FA “double-checks” that the user is valid, MFA “triple-checks”.
It doesn’t matter if your users don’t all work with highly sensitive data or have access to critical accounts; all users should be secured by 2FA or MFA. There are many providers that allow you to enact specific, tailored policies to suit your way of working. To find out more about the best MFA solutions, you can read our article here.



