
50 Web Security Stats You Should Know In 2024
We’ve collated the latest web security statistics to help you keep up to date on the most dangerous web-based threats your organization is facing.

There’s no denying that the internet is an integral part of modern life. Every minute, we as a population send 197.6 million emails, spend 1.6 million dollars online, and download almost 415,000 apps. However, while our ever-increasing use of the internet provides us with endless communication, learning and technological opportunities, it also makes us vulnerable to a whole wealth of web-based threats.
We’ve pulled together the most recent web security statistics from around the world to help illustrate the breadth and severity of the threats facing your organization. These stats come from third-party surveys and reports, and we’ll be updating them as new research emerges to help you stay on top of the latest figures.
The Frequency Of Web-Based Attacks
According to recent research from Verizon, web application attacks are involved in 26% of all breaches, making the second most common attack pattern. However, applications aren’t the web’s only vulnerability. In 2020, global search traffic increased immensely, often spiking during periods of lockdown to combat the COVID-19 pandemic. Now, as the world continues to embrace virtual hangouts and movie streaming platforms for entertainment, and video conferencing tools to communicate with their co-workers remotely, these high levels of global internet usage show no sign of decreasing. While the internet has enabled many organizations to ensure their productivity throughout the shifts to remote and—more recently, hybrid—work, our reliance on the internet makes it a lucrative target for attackers, many of whom focused their efforts on exploiting web vulnerabilities.
Based on an analysis of 7 million websites, SiteLock reports that websites currently experience an average of 94 attacks every day, and are visited by bots approximately 2,608 times a week.
A bot is a software application that runs automated tasks across the internet. These tasks are usually simple and repetitive, so the bots are employed to carry out mundane work that they can complete much quicker than a human could. Some bots are legitimate, such as Google’s crawling and indexing bot. Others, however, are malicious. These bots are employed by cybercriminals to scan websites for vulnerabilities and execute basic attack patterns, such as distributed denial of service (DDoS) and credential-stuffing attacks.
With so many bots tasked with uncovering vulnerabilities, it comes as little surprise—though, still unpleasant news—that an estimated 12.8 million websites are infected with malware worldwide. Search engines often implement blacklisting tools that quarantine suspicious or malicious websites, marking them to users as unsecure and removing them from search results. However, these tools often aren’t powerful enough to detect sophisticated web threats. Because of this, 88% of websites infected by malware are not blacklisted by search engines.
Further research from internet security provider Webroot reports that their engines detect over 26 million IP-related security incidents around the world each day.
Web-Based Attack Methods
According to a recent report, the top 10 countries hosting the majority of high-risk URLs are:
- USA
- Denmark
- The Netherlands
- China
- Russia
- Germany
- Singapore
- South Korea
- Japan
- Canada
In this report, high-risk URLs are classified by the following categories: botnets, keyloggers and monitoring, malware sites, phishing, proxy avoidance and anonymizers, spam, spyware and adware.
Unfortunately, it isn’t always easy to tell that the website you’re visiting is malicious. This is partly because 1 in 10 malicious sites are hosted on an otherwise non-malicious domain. There could be a few reasons for this; firstly, it can be difficult to isolate and block bad content on an otherwise safe domain. Secondly, HTTPS traffic is encrypted, which means that search engine filters have less visibility into the pages hosted on HTTPS websites and may miss malicious content.
The top site categories hosting malicious URLs are:
- Manufacturing (19.87% host a malicious URL)
- Shareware/torrents (11.84%)
- Adult (9.43%)
- Social networking (8.71%)
- Entertainment (8.63%)
- Medicine (7.66%)
- URL link modifier (5.81%)
- Other (28.06%)
While we might expect to see shareware, adult content and social networking sites on this list, we may have to dig a little deeper for the reasoning behind others. Manufacturing organizations, for example, often have complex supply chain relationships, leaving them susceptible to island hopping attacks.
There are two parts to combating this: business IT teams should implement a strong web filter to block malicious webpages from their searches, and the website owner must do their due diligence to protect their website against compromise.
But how do websites host malicious URLs without noticing? Well, the most common way to hide where content really originates—responsible for obfuscating over 96% of malicious URLs—is with the use of URL link modifiers/shorteners. In essence, URL shorteners redirect the user to a page with a longer URL—hiding the URL of the target page until the user has already landed on it.
These target pages could host numerous different threats.
The following table shows the most commonly blocked malicious domains as discovered by WatchGuard’s DNSWatch tool, along with the type of threat each domain contained and the number of hits they received. Note that you should not visit any of the domains listed in this table; doing so will put you at risk of falling victim to a cyberattack. As WatchGuard have in their original report, we’ve put a bracket around a full stop in each link, e.g., “www[.]”, to make the links unclickable.
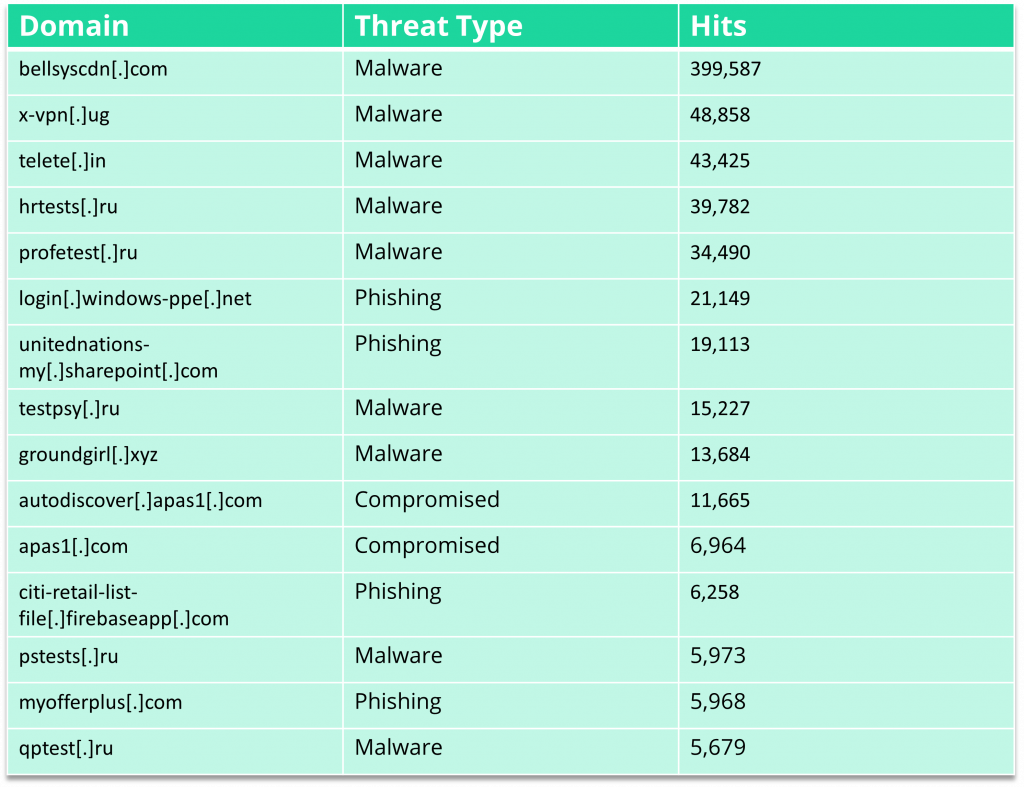
As the table above shows, malware and phishing are two of the most common threat types currently being hosted online. Let’s take a look at each of those in a little more detail.
Web-Based Malware
Over 70% of all system intrusion breaches involve malware, and 32% of all malware is distributed via the web.
The top threats found within websites infected with malware include:
- Backdoor (65%)
- Filehacker (48%)
- Malicious eval request (22%)
- Shell script (22%)
- Injector (21%)
- Phishing (7%)
- Defacement (6%)
- SEO spam (5%)
- Cryptominer (<1%)
And the top malicious web file types that users may be encouraged to download are:
- Exe
- Swf
- Doc
- Apk
- Msi
- Rtf
- Js
- Html
- xls
As well as hosting malware in webpage downloads, bad actors can hack into free public Wi-Fi networks and use that access to install malware remotely onto devices connected to those networks without a VPN.
This is a potential issue caused by remote work when users are accessing corporate systems from insecure devices and Wi-Fi networks. We’ll talk about the risks associated with remote work a little later, but using insecure Wi-Fi connections rather than a direct corporate internet connection is one of the contributors to the fact that personal devices are twice as likely to become infected with malware than corporate-issued devices.
In a recent report, web security vendor Akamai disclosed the threats blocked in 2020 by their Enterprise Threat Protector. Of the 109.13 billion total DNS queries served, Akamai blocked 10,155,209 requests relating to malware, which included malicious links being clicked on a website.
Web-Based Phishing
As well as blocking malware-related queries, Akamai’s report discloses that their web security tool also blocked 6,258,597 phishing-related queries, and gave insights into their own experiences with phishing. According to the report, the platform, finance, global services, CIO office, web sales and marketing units were the most phished business units, and their support, media and carrier teams were also targets of phishing attempts.
Despite this number being lower than the number of malware-related queries blocked, data from Google Safe Browsing shows that there are currently nearly 75 times as many phishing sites as there are malware sites on the internet. This underlines how widespread the threat of social engineering is: 25% of all breaches involve social attacks such as phishing.
According to a recent study, the biggest category of phishing—responsible for 34.7% of all phishing attempts—is targeted towards webmail and Software-as-a-Service (SaaS) users. The same study revealed an increase of 11% in the last year in the number of business email compromise (BEC) attacks sent from free webmail providers—from 61% to 72%. Over half of these used Gmail to deliver their attacks.
But how successful are these attacks? Well, according to Terranova’s 2021 Gone Phishing Tournament report, almost 1 in 5 of all employees are likely to click on phishing links sent via email and, of those, over 70% go on to download a malware file from a phishing website.
The bottom line? 14% of employees are likely to download malware from a phishing page.
So, you know how big the threat is, and how bad actors are implementing web attacks. But who exactly are they attacking? Without further ado, let’s move onto our next section, in which we’ll try to answer that question.
Who The Victims Are
TL;DR—everyone who uses the internet.
Okay, okay, I can feel the eyebrow raise you just gave your screen, so let’s take a look at some specifics.
Let’s start with remote workers. Currently, around 58% of organizations around the world have employees who work remotely, and 74% of organizations intend on shifting at least some of their employees to remote work post-pandemic. Remote work enables flexibility and increases productivity but, without the necessary security measures in place, it can expose your organization to a ream of potential threats. The threats that security professionals are currently most concerned about are:
- Lack of physical security in the workspace (47%)
- Risk of malware infection (32%)
- Criminals gaining control over remote devices to steal sensitive data (24%)
- Securing external comms (23%)
- Securing the network (20%)
- Criminals leveraging devices to gain network access (17%)
- Phishing and social engineering attacks (15%)
- Devices being lost or stolen (12%)
- Securing external access to internal resources (8%)
Note that three of these threats have the potential to involve internet or web access.
In the last year, remote working has increased user access to critical business systems by 59%. However, many users are accessing these systems via an unsecure internet connection.
Unsecure internet networks are a serious threat when it comes to mobile device security, because they enable cybercriminals to carry out man-in-the-middle (MitM) attacks, or trick employees into using malicious Wi-Fi hotspots or access points. A MitM attack is when the hacker intercepts communications between two parties (i.e., the user and the application/system/other entity they’re communicating with), and either eavesdrops on their activity or secretly modifies the data being sent, impersonating the entity the user is communicating with.
One study found that over half of respondents use their mobile phone for online meetings, either as their primary device or secondary to their PC, in order to avoid potential disruption due to an unreliable internet connection. As well as this, 23% of workers use their mobile device as a hotspot when their home internet becomes weak, slow, or stops working altogether. If an attacker were to hack into or spoof the Wi-Fi network that the user is connecting to, they could easily install malware onto that user’s device.
72% of organizations are concerned about MitM attacks and, of those, 23% feel unprepared to deal with those attacks.
Despite the associated risks, the same report found that less than half of organizations prohibit their employees from using public Wi-Fi to perform work-related tasks and that, whether due to dodgy internet connections at home or because of the convenience of working on-the-go, 72% of all employees use public Wi-Fi to work—including 55% of those who work at companies that prohibit doing so!
Another common victim of web-based attacks are organizations who host and deliver their content via content management system (CMS) sites like WordPress. WordPress sites are three times as likely to have malware than non-CMS websites, and 18% of WordPress sites have at least one vulnerability, including SQLI, CSRF and XXS. Installing plugins greatly increases the risk of vulnerability; for every five plugins that you add you your WordPress site, you almost double the risk of compromise. Because of this, you should make sure to remove any plugins that you aren’t actively using.
The Impact Of A Web Breach
The whole reason we want to avoid web-based threats is to mitigate the risk of a data breach. The average cost of a data breach is 4.24 million dollars. That figure reflects an ever-increasing gap in cost between organizations that implement more advanced security processes, and those with less security in place. This means that the cost of a data breach is significantly lower for businesses with a formal security architecture in place, and that it can be devastating for those without this protection.
The same study found that 52% of breaches are caused by a malicious attack, and these particular breaches cost an average of 4.27 million dollars—more than the average data breach. Ransomware and destructive malware breaches cost more than the average malicious attack, because of the way in which they often destroy data. Malicious attacks that destroy or wipe data cost an average of 4.52 million dollars; ransomware attacks cost an average of 4.44 million dollars.
How Can You Protect Your Business Against Web Threats?
As with all aspects of cybersecurity, there is no single silver-bullet solution to web security. We recommend taking a multi-layered approach to defending your network, by implementing a stack of technical and human-centric solutions.
Invest In A Web Security Solution
We’ve found that the most effective methods of web security fall into two main categories: filtering and isolation.
Web filtering platforms protect devices connected to the internet by scanning malicious web code and filtering harmful URLs to prevent data loss. In practice, this means they prevent harmful websites from appearing in search results—most web-filtering platforms feature a pre-configured blacklist of known harmful domains, which they automatically block access to. They also prevent web-based viruses and malware from being downloaded to the user’s device.
Browser isolation platforms isolate each user’s online activity in a secure environment detached (or “isolated”) from their local network. They do this by executing web-based commands in a secure server, or “remote desktop”. This gives the user a completely normal browsing experience, while sandboxing any malicious webpages or downloads within the virtual environment so that they never reach the user’s local system.
Enforce Use Of A VPN
Virtual private networks, or VPNs, create a secret tunnel between the user’s device and the internet. Within this tunnel, the user’s internet traffic can travel safely without being seen by anyone else—be that the user’s own internet provider or a bad actor attempting to gain access to their internet activity.
Corporate VPNs usually connect the user to a corporate server, rather than a server owned by the VPN service. This means that IT admins can view the user’s internet traffic, because they are a part of the same corporate network.
VPNs provide affordable protection to any employees connecting to the corporate network via an unsecured public Wi-Fi network. They also enable employees who are working abroad to access resources as though they were still in their company’s origin country, mitigating the risk of data being blocked by strict internet access laws.
Train Your Employees
71% of organizations that have suffered a data breach in the past year say they could have prevented the breach by implementing better security awareness training.
Security awareness training solutions empower employees to detect and correctly respond to cyberthreats such as phishing by combining bite-sized learning modules that are easy to complete around a work schedule, with active testing and attack simulations.
The strongest security awareness training platforms enable admins to centrally manage their employees’ training, and produce detailed reports into training success at both an individual level (to assign further training when necessary) and an organizational level (to prove ROI).
Want to find out more about how you can protect your network? Check out our buyers’ guides to the top security solutions that will help you defend against web-based threats:



