Twingate
Twingate enables organizations to easily provision secure, remote access to corporate resources without compromising the user login experience.

Expert Insights Verdict
Twingate is a highly effective zero trust network access solution that enables organizations to easily provision secure, remote access to corporate resources without compromising the user login experience. The platform offers highly granular access policy configurations and detailed activity logging, making it suitable for organizations operating within highly regulated industries such as legal, finance, and healthcare. However, this granularity doesn’t cause complexity; Twingate’s interface is intuitive and navigable, and the solution is easy to deploy with little specialized technical knowledge required.
Pros
- Granular access policy configurations
- Detailed logging and reporting of user access activity
- Seamless access experience for end users
Cons
- No managed deployment service—but deployment should be easy for most organizations without this
Overview
Twingate is a cybersecurity provider that allows IT, security and DevOps teams to enable secure, remote access to corporate resources. Twingate’s eponymous SaaS platform is a replacement for legacy VPN solutions, building enterprise-grade security and a user-friendly interface that enables businesses to set up a software-defined perimeter and centrally manage access to company applications—on-prem and cloud-based—without changing their IT infrastructure.
Twingate is delivered as-a-Service, with a downloadable Client software application that must be installed on end user devices. The platform is managed via a single web-based admin console, from which admins can configure policies to automatically grant or deny user access based on their identity, device, and login context.
Twingate: Getting Started
Key Features
Zero Trust Network Access
Twingate connects users to applications via their FQDN or IP address. All user connections are encrypted end-to-end to prevent unauthorized viewing of a user’s web activity. The platform also offers native two-factor authentication via time-based one-time passcodes, as well as integrations with third-party identity and access management tools, to protect against credential-related breaches. All access requests are granted or denied based on real-time contextual information including user identity, device security posture, time of login, and user/device geolocation, and according to admin-configured access policies.
The security offered by Twingate doesn’t compromise the end user’s experience. Split tunnelling and intelligent routing direct all traffic for sensitive resources through dedicated encrypted tunnels, reducing the strain on bandwidth and eliminating backhauling, to give users a faster, more reliable connection than is available via a legacy VPN.
Granular Access Policies
From Twingate’s web-based management console, admins can provision and deprovision users, view reports into resource usage, and configure granular access policies. Access policies can be configured on a per-use, per-device, and per-resource basis, allowing admins to enforce the principle of least privilege to help prevent account takeover attacks, and achieve compliance with data protection standards that require heightened protection of privileged accounts.
Because access controls are placed on routes at the port level, rather than giving users permission to the entire network, Twingate enables businesses to limit the lateral spread of cyberthreats, as well as gain better visibility into user access across their network.
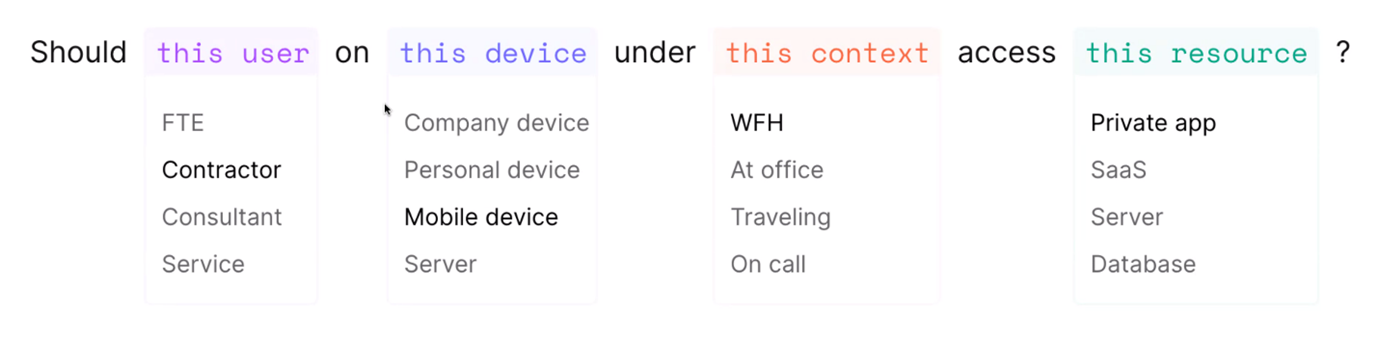
Conditional access policies in Twingate
Logging And Auditing
Twingate logs all network activity, including identity-indexed logs into what each user has tried to access or connect to. This provides detailed insight into access at the resource level, which can be used to identify and remediate malicious behavior, as well as monitor application usage and remove unnecessary subscriptions.
The platform also offers integrations with Data Dog, Elastic, and Splunk for heightened logging and reporting functionality. Reports are easy to generate and navigate through the admin dashboard, and are visualized for at-a-glance analysis of access trends.
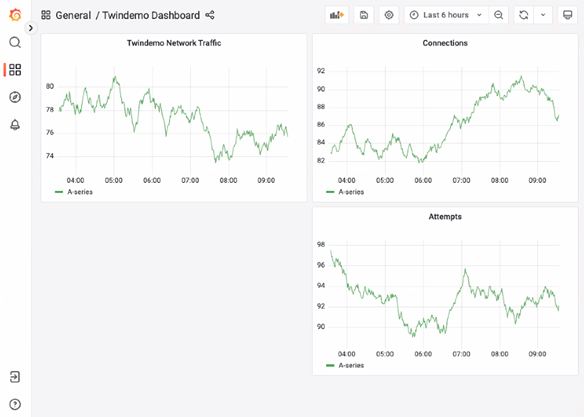
The connection and traffic dashboard in Twingate
Wide Range Of Integrations
As well as offering integrations with SIEM solutions and log managers, Twingate integrates seamlessly with a wide range of identity providers— including Okta and OneLogin —to support MFA and single sign-on across all user accounts.
Twingate also integrates with a number of mobile device management and endpoint detection and response vendors for ease of management and clearer visibility across various layers of security.

Twingate's supported integrations
Ease Of Use
Twingate does not currently offer a managed deployment service, but the platform deploys as-a-Service in around 15 minutes via API. The Twingate Client must also be installed on each end user device for user authentication and access authorization—this involves a straightforward installation process, and the Client is compatible with iOS, MacOS, Windows, Android and Linux devices.
The platform’s variety of integrations makes initial implementation straightforward, enabling many organizations to deploy Twingate without having to make changes to their existing security architecture.
Overall, Twingate’s user interface is highly intuitive and easy to navigate. Setting up new access policies is straightforward, and the reporting tools are very accessible.
Pricing And Plans
Twingate is available via three packages:
- Starter supports individuals and small teams of up to five users, offering secure remote access with a support community
- Business supports up to 150 users, with more granular access controls and additional email support
- Enterprise supports an unlimited number of users, with additional network analytics and priority support
Pricing for each plan is available upon direct request via Twingate.
Best Suited For
Twingate provides enterprise-grade security without compromising on usability. The lightweight, intuitive solution is well-suited to smaller businesses and mid-sized enterprises looking to easily provision their remote users with reliable, secure access to corporate resources. Its protection for apps hosted in various cloud environments (AWS, Azure, etc.) also make Twingate suitable for securing access for DevOps professionals. Finally, Twingate’s granular access policies enable it to support organizations in highly regulated industries, including financial services, healthcare, and legal services.
Twingate doesn’t offer on-premises deployment, so is best suited to cloud-native organizations, particularly those already using a range of cloud-based security tools for endpoint, identity, and web security.
Final Verdict
Twingate is a highly effective zero trust network access solution, enabling organizations to easily provision secure, remote access to corporate resources without creating friction within the user login experience.
The platform offers highly granular access policy configurations and detailed user activity logging, making it suitable for organizations operating within highly regulated industries. However, this granularity doesn’t cause complexity; Twingate’s interface is highly intuitive and navigable, and the solution is easy to deploy with little specialized technical knowledge required.
We recommend that any SMB or mid-sized enterprise looking to provide remote end users or DevOps professionals with secure, remote access to corporate resources, consider shortlisting Twingate.
Company Information
Enterprise VPNs
twingate.com
2018
Redwood City, CA
Cloud
SMB, mid-market
Twingate Awards









