
Protecting Your Passwords In The Office And Beyond
Sponsored Content: How to protect your business passwords in the workplace – whether your employees are in the office, at home, or on the go.

In the last 12 months, many of our workplaces have changed almost beyond recognition. Who could have predicted back in January 2020 that we’d be trading our suits for sweatpants and our air-conditioned offices for messy kitchen tables? But unfortunately, figuring out how to unmute themselves in a Zoom meeting isn’t the only problem that remote workers have encountered over the past year.
Managing employee passwords and account access is one of the most significant security challenges posed by a rapid move to remote working. Stealing corporate data can be a lucrative industry for hackers, who either sell that data on the dark web or threaten to expose the victim organization’s secrets unless they pay a ransom. Combine this with the fact that employee passwords are the keys to the kingdom of company data and financial information, and you begin to understand why credential theft can be an easy “in” for bad actors trying to access that data… especially if those credentials aren’t properly secured.
This means that poor password practice is one of the biggest causes of data breaches that organizations are currently struggling with, and this risk is exacerbated when employees are working remotely, using devices and internet connections which are less secure.
On top of the technical insecurities of remote work, employees tend to be less cyber-aware when working from home. While many organizations regularly test their employees with rigorous security awareness training and phishing simulations, there are also many that don’t. Unfortunately, it’s easy to forget the security training you completed with a cat walking across your keyboard and a seven-year-old clamouring for help with their math homework in the next room!
Switching to remote work can make data loss prevention far more challenging, say 84% of IT leaders, particularly if you don’t implement the right security measures. But in order to improve your password security across a volatile working environment, you first need to understand why your employees are your biggest vulnerability when it comes to data loss. We’ll begin by exploring the most major threats they’re facing in the workplace.
What Are The Most Common Attacks Your Employees Are Facing?
There are three main threats to password security currently storming the digital world: brute force attacks, phishing, and business email compromise. Let’s take a look at each of them in a little more detail.
Brute Force Attacks
Brute force attacks are some of the easiest for hackers to carry out, which is why they’re so common. The bad actor assigns a computer program to guess the password to a user’s account, starting with passwords known for being commonly used, and gradually working through all possible combinations letter by letter until it cracks the password. Spraying attacks work in a similar way, except that they target thousands of accounts at once across multiple organizations, whereas traditional brute force attacks tend to focus on one account at a time.
The weaker a password is, the quicker it is for a hacker to gain access to that account using one of these automatic cracking techniques.
Phishing
Phishing is a type of cybercrime based on email fraud. A bad actor emails their victims while posing as someone they know, in the hope that they’ll trick that victim into giving them sensitive data such as financial information or login credentials. Phishing attacks are a type of social engineering – they rely on human error to succeed. This makes them particularly effective in times of uncertainty, when we’re more likely to have other things on our minds and therefore more likely to make mistakes.
Phishing attacks can only be successful if people are falling into bad habits when it comes to their password practices, such as giving away account credentials without double-checking the identity of the person asking via a second method of communication. The habit of reusing passwords can also increase the damage caused by a successful phishing attack, because the bad actor then not only has access to the account they were initially targeting, but all further accounts “secured” with the same credentials.
It comes as no surprise, then, that phishing attacks have increased dramatically over the past year as people have grappled with the challenges presented by global pandemic and the switch to remote working and, in doing so, forgotten their password hygiene training.
Business Email Compromise
Business email compromise (BEC) attacks are an extension of phishing attacks and other types of credential theft that don’t rely on human interaction, such as brute force, dictionary and spraying attacks. Once a bad actor has successfully hacked into a corporate email account, they begin impersonating the real account owner. In this disguise, the attacker manipulates the company and its stakeholders into sending them money or sensitive data.
These attacks spread laterally and can result in not only the original target organization suffering financial and reputational damage, but can also lead to devastating consequences for their customers, clients and partners, too.
Like phishing and brute force attacks, BEC attacks can only be successful when an organization isn’t vigilant about how its employees are using passwords. If proper practices are implemented, the risk of falling victim to an attack is greatly reduced.
In order to defend ourselves against these sophisticated, targeted attacks, we first need to understand what vulnerability hackers are exploiting to carry them out. And that brings me on to…
The Root Of The Problem
The three attacks outlined above all have something in common: credential theft. Your employee may have handed over their credentials willingly to someone they believed to be a trusted source, or the attacker may have stolen them through a brute force attack. Either way, those credentials are the key to your organization’s data. Once the attacker has that key, they can cause irreparable damage not only to your company’s infrastructure and finances, but also its reputation.
Unfortunately, we as a global workforce are notoriously bad at keeping our keys safe, and poor password practices only make it easier for attackers to gain access to our accounts – so much easier, that 81% of hacking-related breaches involve credential theft, according to a 2020 report by Verizon. But what exactly are we doing wrong?
Cause One: Reusing Passwords
The first mistake that many of us make is in reusing passwords across multiple accounts. A recent study from password management vendor Dashlane found that 30% of workers reuse business passwords, and 22% use the same passwords across personal and business accounts. Further research has shown that, when enforced to reset their password as a part of corporate policy, 49% of employees just reuse the same password with a minor change, such as an extra character.
“But my password is eight characters long, and has a number, a capital letter, and a special character!” – your employees may protest. Alas, the typically enforced eight-character password, no matter how “complex” it is, can be cracked relatively easily in under three hours with the right computer. So if an employee uses the same password for multiple accounts, a bad actor could gain access to every one of those accounts in as long as it takes to watch an episode or two of Black Mirror.
Cause Two: Sharing Passwords Insecurely
Secondly, many of us have developed the bad habit of sharing passwords insecurely, by sacrificing security for ease and speed. We’re always told never to share passwords with anyone at all, but at work it’s inescapable – multiple people may need to access a single account due to licensing costs, or working on a project together. In organizations that don’t have a secure password sharing system in place, employees often keep track of login credentials on a shared spreadsheet or, when in the office, on a post-it note slipped across the desk.
With more people currently working remotely, the post-it isn’t an option – which means that people are turning to instant messaging apps or emails to share passwords. Now, the post-it was never a secure way to share passwords especially not if you leave them stuck to your monitor rather than throwing them away)… But sending them via Slack or an unencrypted email can be even less secure, because then the password exists in that user’s digital footprint. If a hacker were to access their inbox or messaging app, they’d instantly be able to access that shared account, too.
On top of that, spreadsheets, sticky notes and instant messages as a means of password sharing pose a problem in terms of account management. This is because IT admins can’t have a clear overview of which users hold passwords to which accounts and licenses.
Cause Three: Creating Weak Passwords
Finally, and perhaps most simply, our passwords just aren’t strong enough! This one is mostly down to laziness and the inability – or unwillingness – to memorize a complex password or passphrase for every account we have to log into. And when you take into account that the average internet user has 150 accounts to keep track of, it’s easy to understand why. Unfortunately, as the digital world continues to expand, this number will only increase. Already, 80% of organizations are chasing digital transformation more quickly than they can improve their security practices and infrastructure to defend against cyberattacks.
However, just because we can understand the challenges of implementing good password practices doesn’t mean that we should excuse bad ones. Yet, it will still come as an unwelcome surprise to some technicians that “123456”, “password” and “qwerty” are still consistently topping lists of most commonly used passwords. Thankfully, there’s an easy way to keep your employees’ passwords strong, secure, and – most importantly – a secret.
How To Protect Your Employees… No Matter Where They’re Working
Business password management solutions help organizations to protect their employees’ passwords and manage the access to all corporate accounts. They enable users to generate and securely store strong passwords, and synchronize all passwords across all of the devices they work on, including personal laptops, smartphones and tablets. This means that each user’s credentials, for each of their accounts, are strong and secure, no matter where or on which device that person is working.
All password management solutions have a key piece of technology at their core that enables them to offer this protection: a password vault. Each employee has a personal vault that stores their login credentials in one place, so that they can access them easily without having to remember them all or search through chat histories to find them. All information stored in the vault is encrypted with a key called a master password. This master password, like the vault itself, is unique to each user, and it’s the only password they need to memorize to be able to access all of their accounts.
A password manager like Dashlane also includes the functionality to set up Business and Personal Spaces. These spaces allow users to store their business and personal credentials separately within their vault, eliminating the security risks posed by employees reusing personal passwords for business accounts. This is particularly useful in today’s world, where employees are increasingly working across multiple devices, including their own personal ones; separate account spaces allow users to keep on top of password security no matter whether they’re working in the office, from home, or on the go.
Once a user has signed in to their vault at the start of their session, the password manager automatically fills in all web-based login forms using the credentials stored in that user’s vault. If the user comes across a form that they haven’t got an existing account for, the manager generates a completely random password and automatically adds it to the vault.
Although all password managers offer this core vault technology, some go a step further towards keeping your organization’s data safe from both internal human error and external threats, by implementing further security features.
Secure Password Sharing
The first key feature that a strong password management solution should offer is the capability to share passwords securely from within the password vault. Dashlane’s business password manager includes a feature that simplifies and secures the process of sharing credentials among users. Within the vault, the sender selects the password they wish to share, then selects the user they wish to share it with, and finally clicks “send” – it’s as easy as one, two, three. If a user needs to send credentials to multiple others at once, an admin can set up a password Sharing Group, which gives the administrators a complete overview as to who has access to which corporate accounts.
Password Health Reporting And Analytics
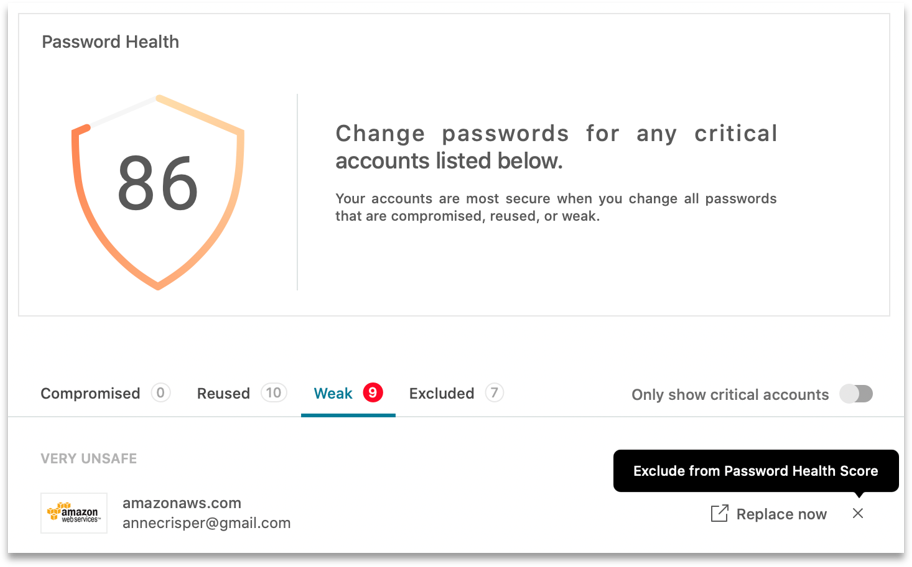
Dashlane also includes an easy to use, centralized admin console. From the console, admins can manage their subscription and configure policies such as enabling or disabling auto-filling, VPN settings, two-factor authentication (2FA) enforcement – we’ll talk about that more in a minute – and setting up Business and Personal Space domains.
The console also features robust reporting and analytics, generating detailed reports into account usage, shared password information and Password Health reports. These reports give admins an insight into the strength of each user’s passwords, and enables them to track corporate password health over time. But this feature isn’t only for admins – employees can also check their own “health scores” and see whether their passwords ae weak, duplicated, or have been compromised, and update them accordingly.
Multi-Factor Authentication
Finally, as promised, Dashlane comes with built-in 2FA. Two-factor authentication is a method of user access management that requires users to verify their identity in two ways to be able to sign in to their account. This secondary method of authentication could be something the user knows, such as the answer to a security question; something the user has, such as a code generated by an authenticator app; or something the user is, which involves their biometric data, such as a fingerprint scan. Asking for further verification means that a hacker won’t be able to gain access to a user’s account, even if they’ve managed to get hold of their password through a phishing or brute force attack. If you know that 31% of Americans use their pet’s name as their password, for instance, you might be able to hack into an account after five minutes scrolling through your victim’s social media channels. It’s much more difficult to scan their fingerprints without them knowing.
View Dashlane Plans
Summary
Storing passwords in an Excel spreadsheet or pinging them across to a co-worker on Skype just isn’t secure enough to protect your organization against advanced cyberattacks. And if that’s not enough, just imagine the logistical nightmare of trying to manually manage all of the account credentials that are linked to your corporate domain… 150 passwords per employee can quickly add up to a mountain of data to keep track of. But no pressure, right?
Wrong – because each of those data points is a key to your organization’s network. That’s why we recommend implementing a strong password management solution like Dashlane, which makes managing account credentials simple, quick and easy, both for admins and end users. Dashlane ensures that all of your employees are using strong passwords across every one of their accounts, and encrypts each of those passwords securely for extra protection against bad actors trying to access your systems.
Your employees might be returning to the office post-pandemic; your organization may have embraced the culture of remote work permanently; or you may have decided on a hybrid combination of the two. A business password management solution will help keep your workplace secure – no matter where that workplace is.



