
Conditional Access Management: Everything You Need To Know
Conditional Access policies grant access depending on factors like location and device. How do conditional access policies work, and how your organization can implement them effectively.

Conditional Access is used to describe security and access policies that are dependent on specific factors. Rather than letting any user access a site or area, access will be prevented unless specific criteria are met.
Now, technically most digital accounts provide a degree of conditional access – if you don’t have the correct username and password, you are not granted access. That is the condition. When we talk about conditional access, however, we are referring to a more advanced and nuanced set of factors to allow or deny access.
How Do Conditional Access Policies Work?
Conditional access policies are built around configurable statements that decide how a solution should respond to a given scenario. These solutions ingest data, compare it with the policy statement, then respond accordingly. We tend to call these inputs signals. Common signals might include user, location, device, application, and risk.
These factors will lead to a policy statement having a different outcome. For example, a policy statement may be “If account access is requested from a known device, then allow access”. This statement could be complimented by other, subsequent policies. “If account is requested from an unknown device, then validate identity through MFA before allowing or denying access”.
Other signals include:
Device
The most obvious device-based conditional access policy ensures that a login attempt is coming from a recognised or known device. If a login request comes from an unrecognized device, the solution may ask for another factor of authentication before granting access.
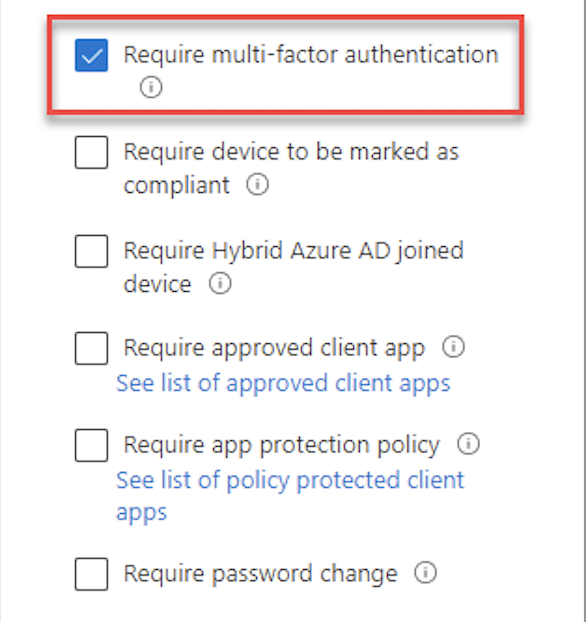
You can also customize policies to
- Require multi-factor authentication
- Require device to be marked as compliant
- Require approved client app
- Require app protection policy
Location
You may require that users only access services or data from specific geographical regions. This can be as broad as entire countries, or as specific as an IP address. You may only want to grant access whilst in the office (and therefore connected to the local IP) or prevent access when out of the country. Both these factors are possible through conditional access policies.
Time
This is often a useful means of indicating if an access request is from a valid user, or if an account has been compromised. Access solutions can create baseline profiles of normal behavior. If a login request is delivered at an unusual or abnormal time, access can be blocked.
Type of access request
It may be that a user is attempting to log into an area they do not usually access, or do not have authorization to. The user may be granted permission by contacting an administrator. Alternatively, they may have “read only” access that prevents them from editing or downloading and saving documents.
Contextual risk factors
By using the unique baselines generated through user analysis and contextual awareness, access solutions can make a judgement as to whether granting user access will be a safe or risky decision. These solutions often assign users a risk score, which changes over time, and in response to a range of factors.
These inputs can be assessed in isolation, or in conjunction with multiple signals. Admins will specify how a solution should respond, depending on each input. There are a range of responses available to admins to achieve several aims. Security can be prioritised through blocking access, while enforcing MFA can look to confirm a user’s identity. The most common response actions include:
- Allow access
- Require MFA
- Limit access (to specific content, or to read only access)
- Reset password
- Monitor access
You may see some providers referring to precedence or conditional hierarchy, this is used to decide what outcome is most relevant when multiple access policies are in play. When there are overlapping policies with different outcomes, the most restrictive policy will be chosen. This means that data that needs to be kept secure is kept secure, while less restricted data will also be blocked.
In this scenario – of overlapping policies – security will be preserved, at the detriment to usability. Some actions that should be allowed, will actually be blocked. It is, then, important to make your access policies as specific and focused as possible. This will ensure that the most appropriate policy is active.
The hierarchy tends to put “deny” as the dominant action, followed by “allow access with MFA”, then “allow access without MFA” as least important.
What Are The Benefits Of Conditional Access?
- Enhanced Security – Enforce robust and effective security policies to secure your accounts and users.
- Improve User Experience – Intelligent analysis only requires additional identity confirmation when necessary, rather than by default. This reduces the burden on the user, making their experience smoother.
- Increased Flexibility – Ensure that the correct users are granted secure access from any location or device (if your policies permit).
What To Look For In A Conditional Access Solution
While you always want to have a good deal of flexibility and configuration with any cybersecurity solution, conditional access is an area where it helps to have pre-sets. Conditional access can be very complicated to implement in practice – there are so many variables to be aware of and to consider.
To ensure that your solution is usable and effective, it is best to look for a solution with a user-friendly policy builder. This will give you a clear dropdown menu with elements that can be customized. Admins can then select a conditional factor and select the desired response.
Microsoft Azure is one such solution. When building a conditional policy, Azure provides a clear menu of possibilities. Admin can easily select the correct response – in this case to “Require MFA” – in response to a specific factor. This simple design and UI makes it easy for admins to implement advanced and effective security controls.
That being said, organizations decide to use a conditional access solution because it gives them additional control over access and security. If a solution does not provide enough flexibility, it will be ineffective.
Before committing to a conditional access solution, it is worth considering the factors that you want to manage access, and checking the solutions that offer this capability.
Conclusion
Conditional access policies are a highly effective means of tightening security infrastructure, without investing in further tools, or asking your employees to drastically change their behavior. Through implementing precise and accurate conditional access policies, you tailor the security and user experience depending on specific circumstances – this ensures that when risks are low, users can carry on unimpeded. However, when there is an anomaly, or another reason to be cautious, the platform will ramp up security.
While conditional access has the potential to be complicated and advanced, many of today’s access management solutions simplify the process, allowing organizations of all types and experience levels to implement this type of security.






